Approaches to Session Hijacking
1. Session Fixation
The attacker pre-determines the session ID that the victim will use. Ex. the attacker could send the victim a link with a predetermined session ID & that link might require the victim to log in. After the victim login, the attacker could impersonate (pretend to be [another person] for entertainment or fraud) the victim.
2. WeakEncryption/WeakSessionCookies
It can be that the website transmits the passwords as plain text or weak encryption that can easily be reversed. Cookie values should be random and unpredictable to ensure they can’t be guessed.
TryHackMe (OWASP TOP 10 [Task 7])
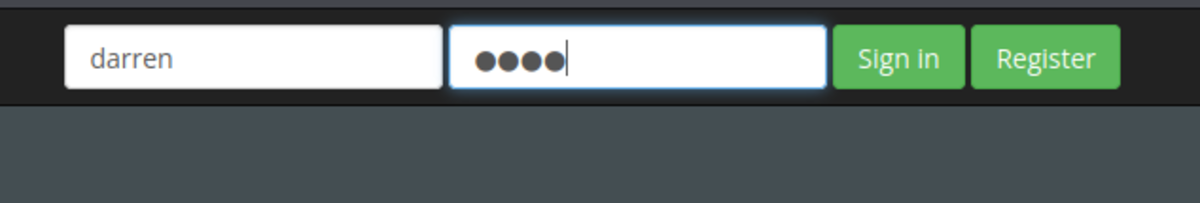
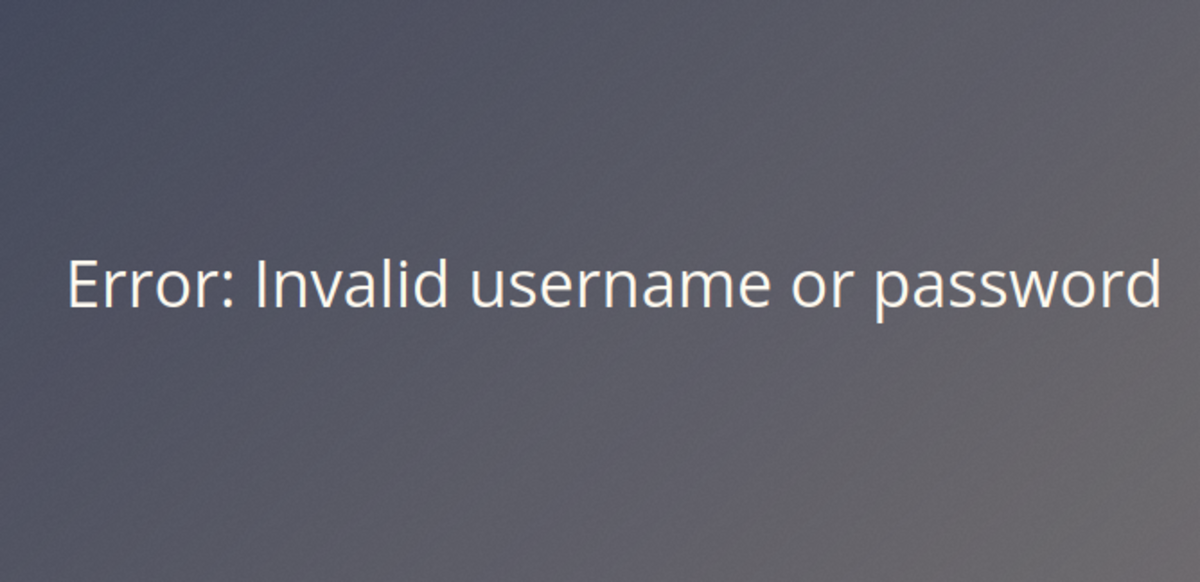
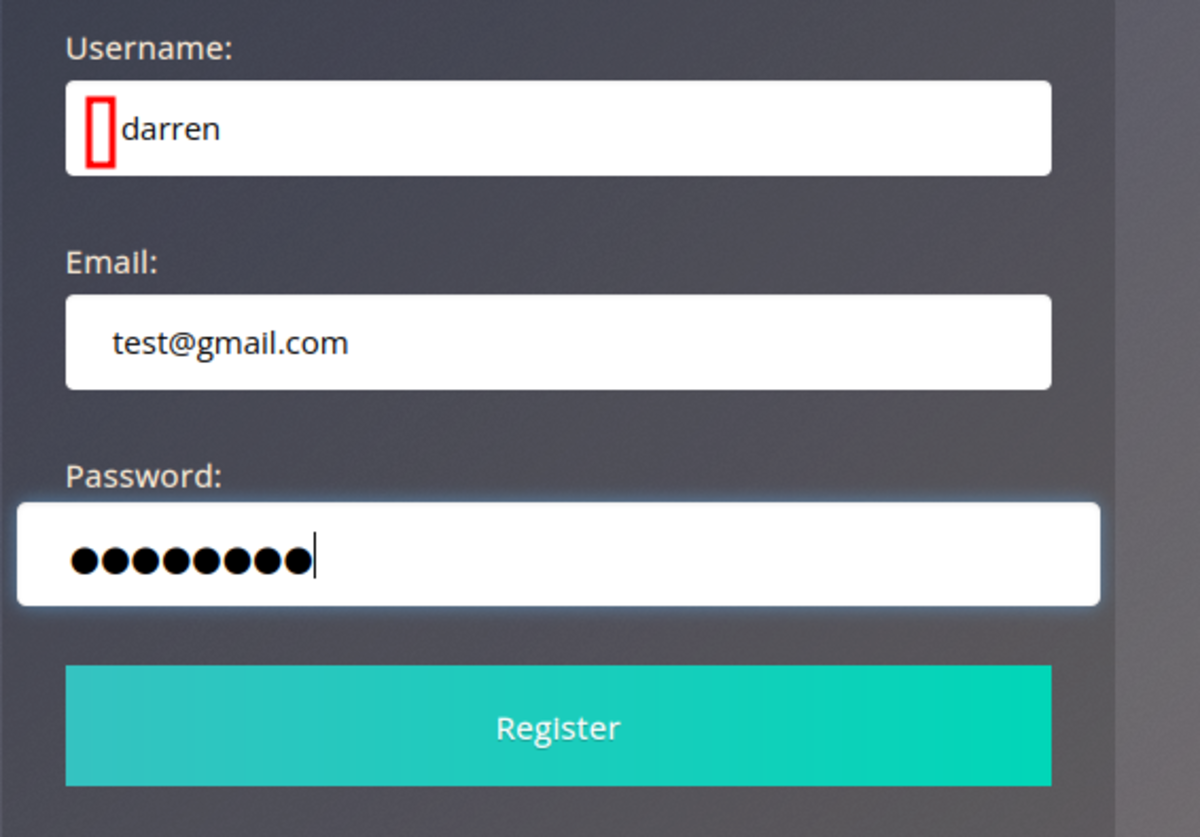
If this is your first time working on TryHackMe and you don’t know how to set it up, then check out the bonus resource section at the end. Navigate to: https://tryhackme.com/room/owasptop10 Task 7 Let’s try to sign in with username- “darren” & password- “test” Isn’t it quite obvious? Now let’s re-register the same user but with a space. Now try to login. Done !!!
OWASPBWA
(Vulnerable Machine Link and setup video in the bonus resources)
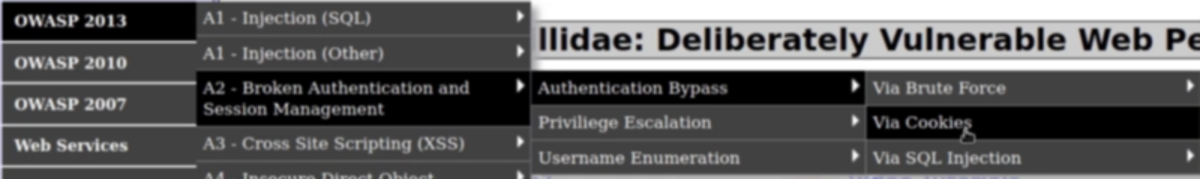
1. Broken Authentication via Cookies
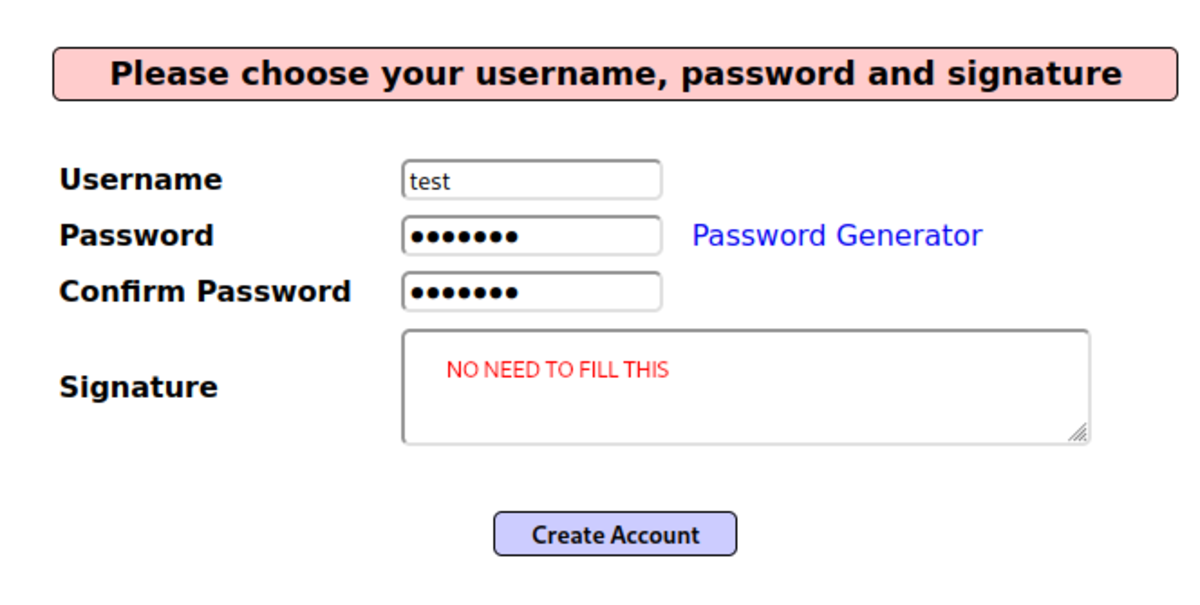
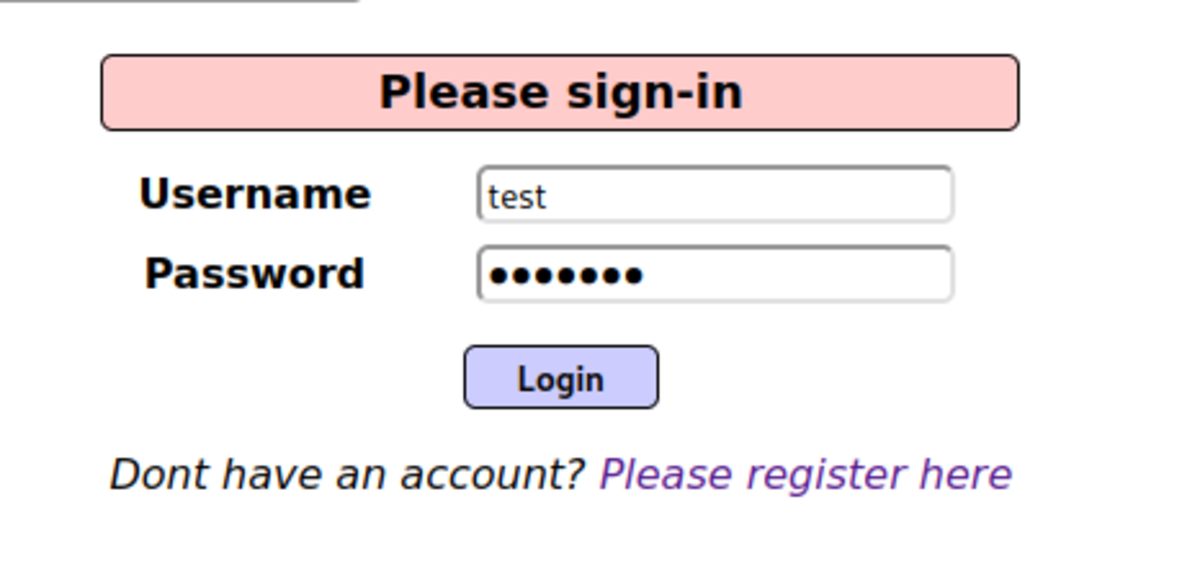
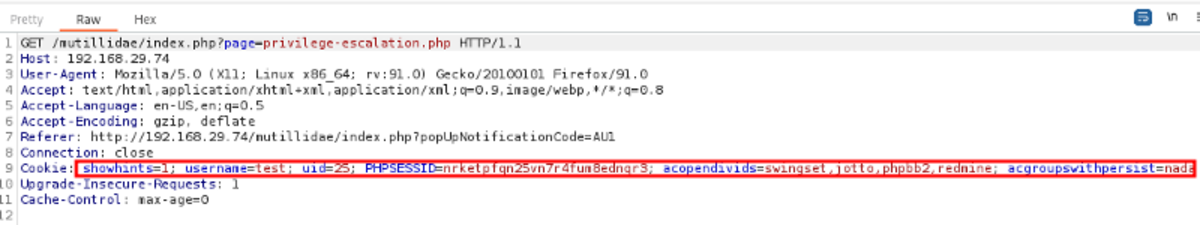
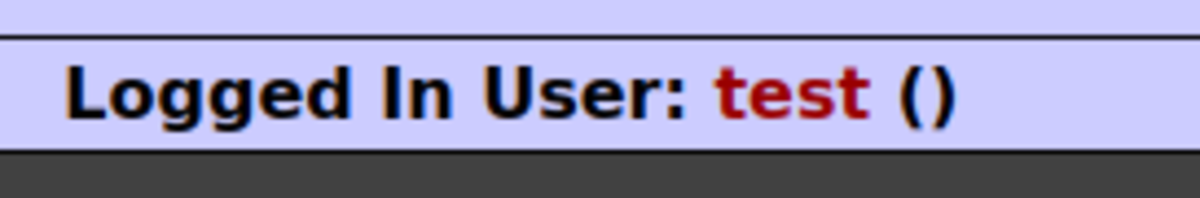
Navigate to: OWASP 2013 →A2 -Broken…Management →Authentication Bypass →Via Cookie First, we need to create an account. Log in with the username & password you used in the previous step. Now go back to the page and try to bypass and switch the account by changing the value in the cookies field. Turn on the intercept in the burp suite and refresh the page. Two interesting fields are ‘username’ & ‘uid’. Attempt 1: Changing the username to “admin” and forwarding the request Nothing happened we are still logged in as a ‘test’. Attempt 2: Changing the UID Let’s change it to ‘1’ BOOM !!! Logged InSummary: This vulnerability allows us to switch accounts by changing the user ID in the cookie field.
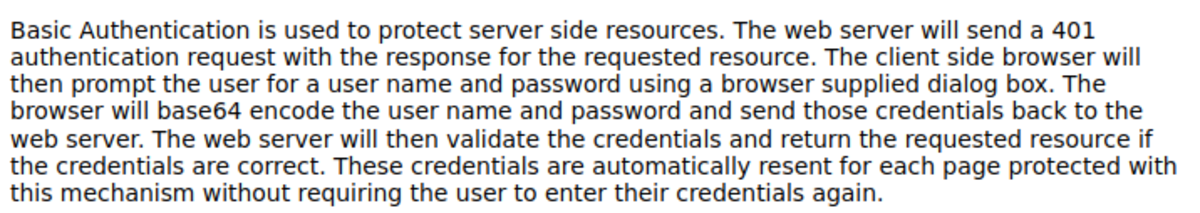
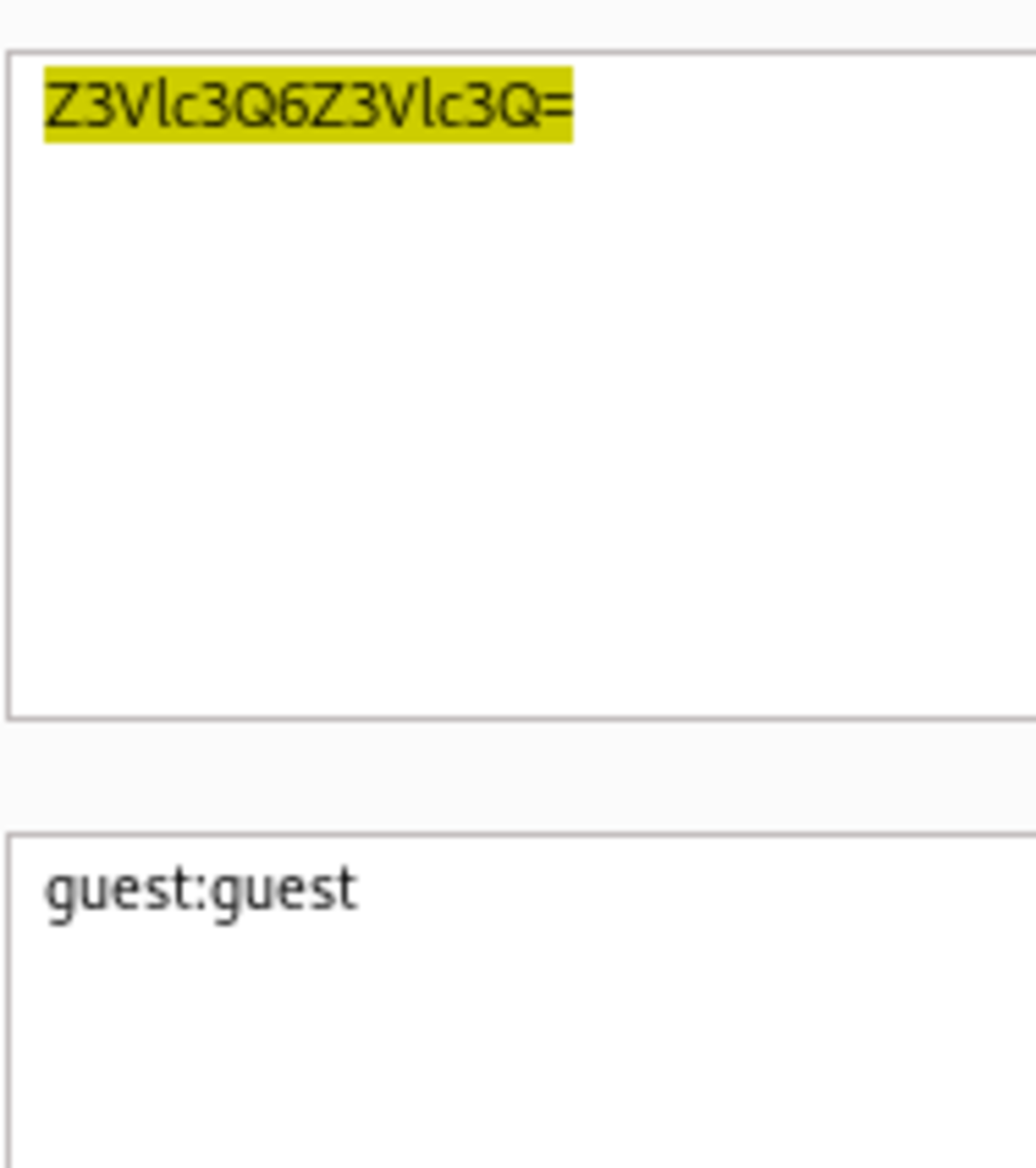
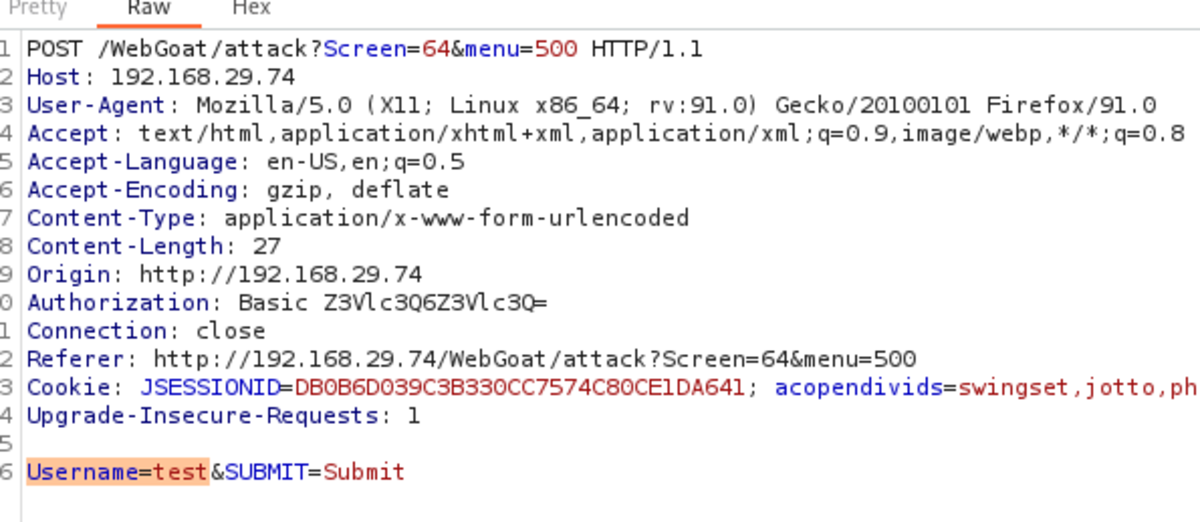
2. Basic Authorization in HTTP Request
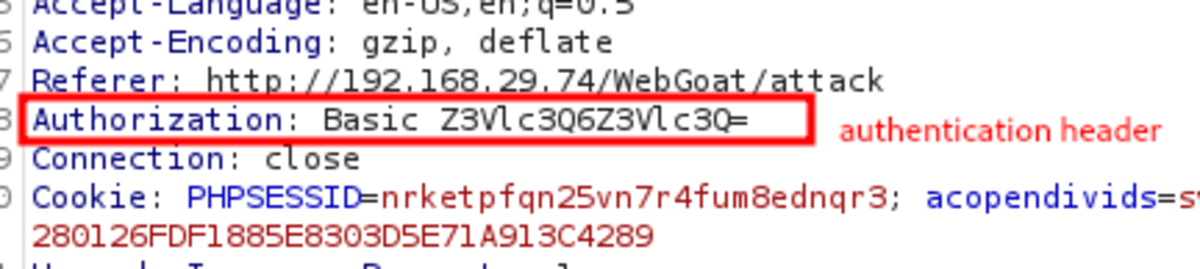
This one is aimed at alteration within the page. Username=’guest’ & passwd=’guest’ Base64 encoding is weak and can easily be decoded (trick to identify: ‘=’ sign at the end). Now turn on the intercept and refresh the current page. decoded base64 value
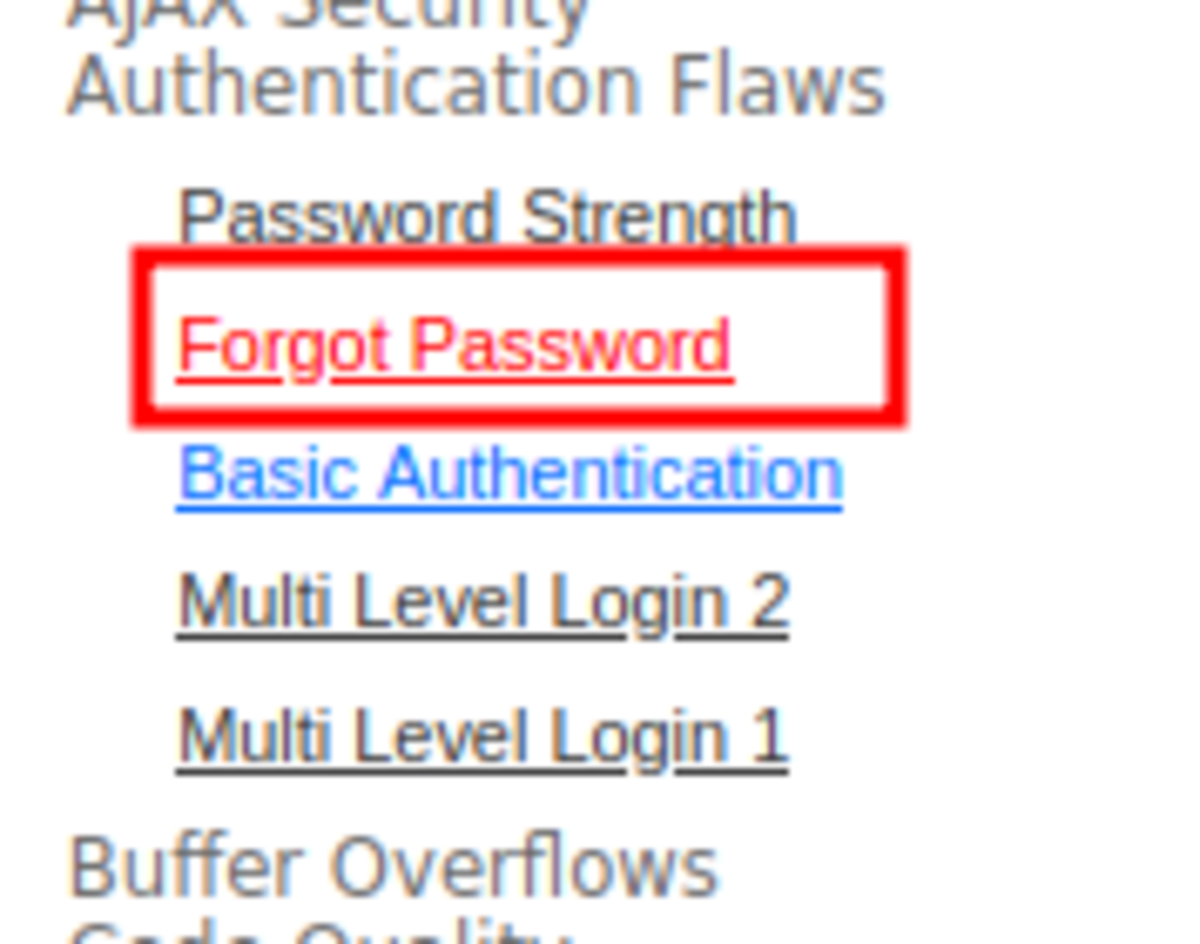
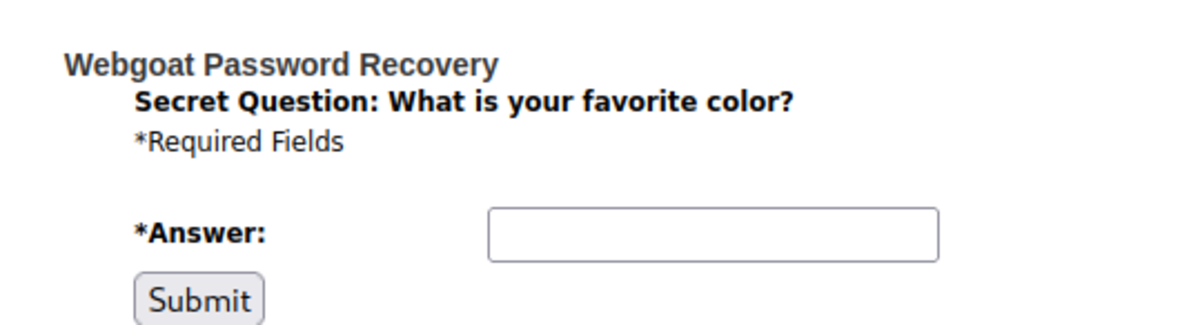
3. Forget the Password
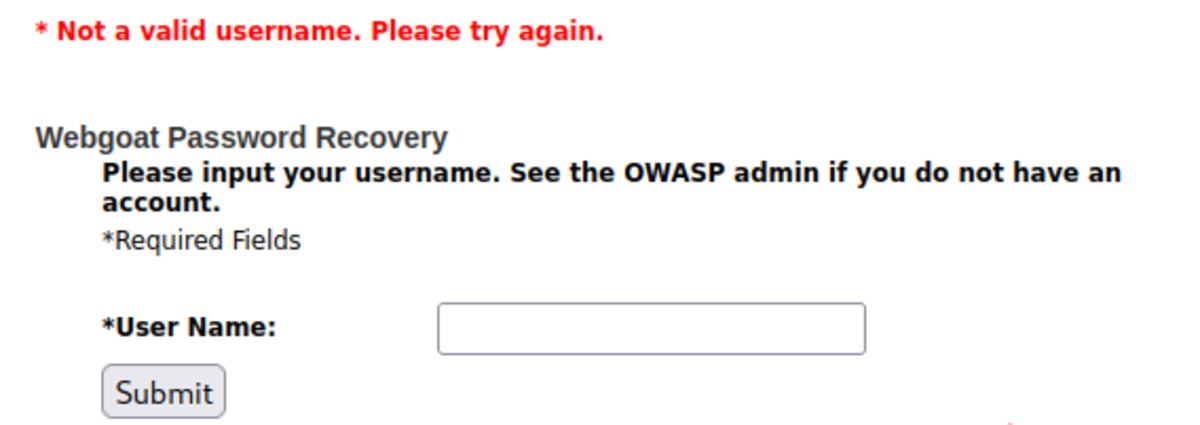
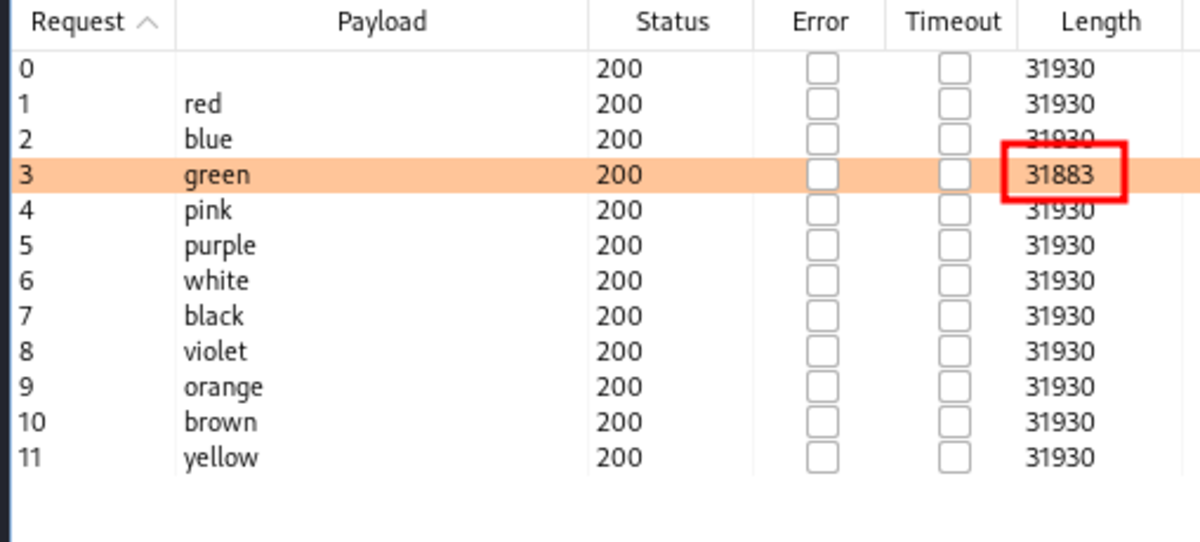
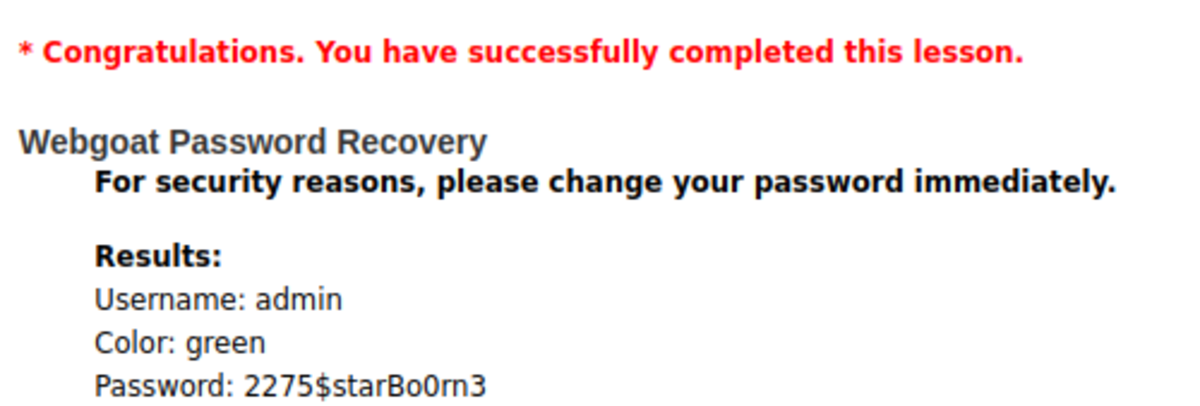
Turn on the intercept, type any username, and press the Submit button. Send the intercepted request to the intruder and ‘clear $’. After turning off the intercept, we can see that the username is invalid. Now we are going to brute-force the username and the secret question. For payload — /usr/share/wordlists/metasploit/http_default_users.txt All the status codes are 200 but the length for the username admin is something different (Hmmmmmm…) Right-click on that, and then show the response in the browser. Now, we need a secret question for username admin that we just found. As it’s a widespread question, let’s brute force it with our worklist. Summary of this vulnerability:
The webpage doesn’t block us after certain incorrect requests. The secret question is too easy and we guessed it in a few seconds.
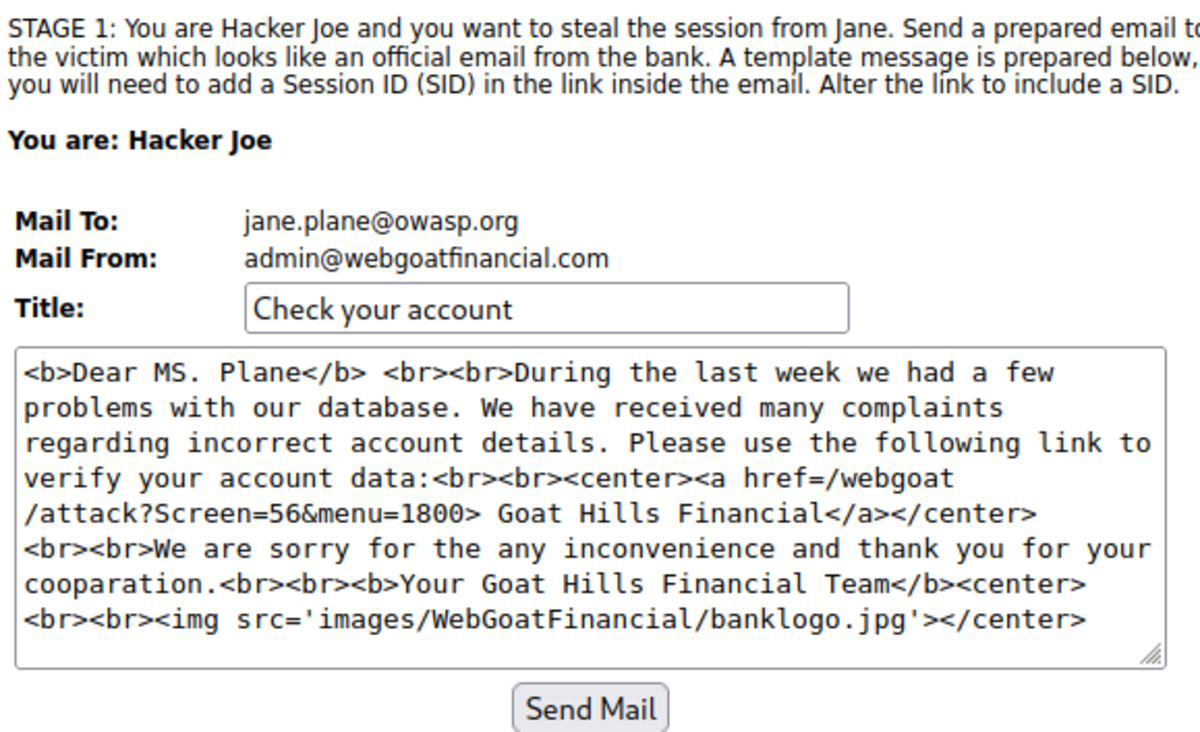
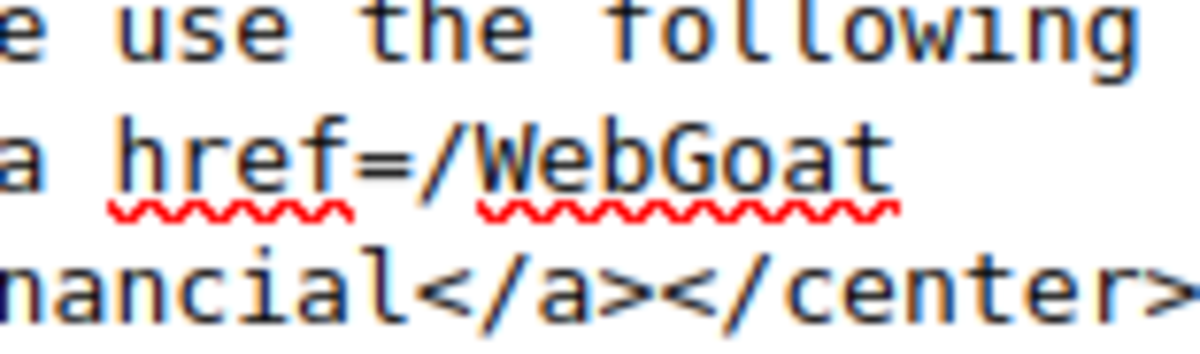
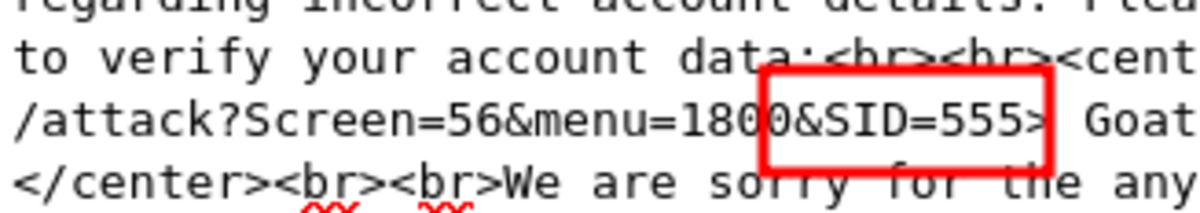
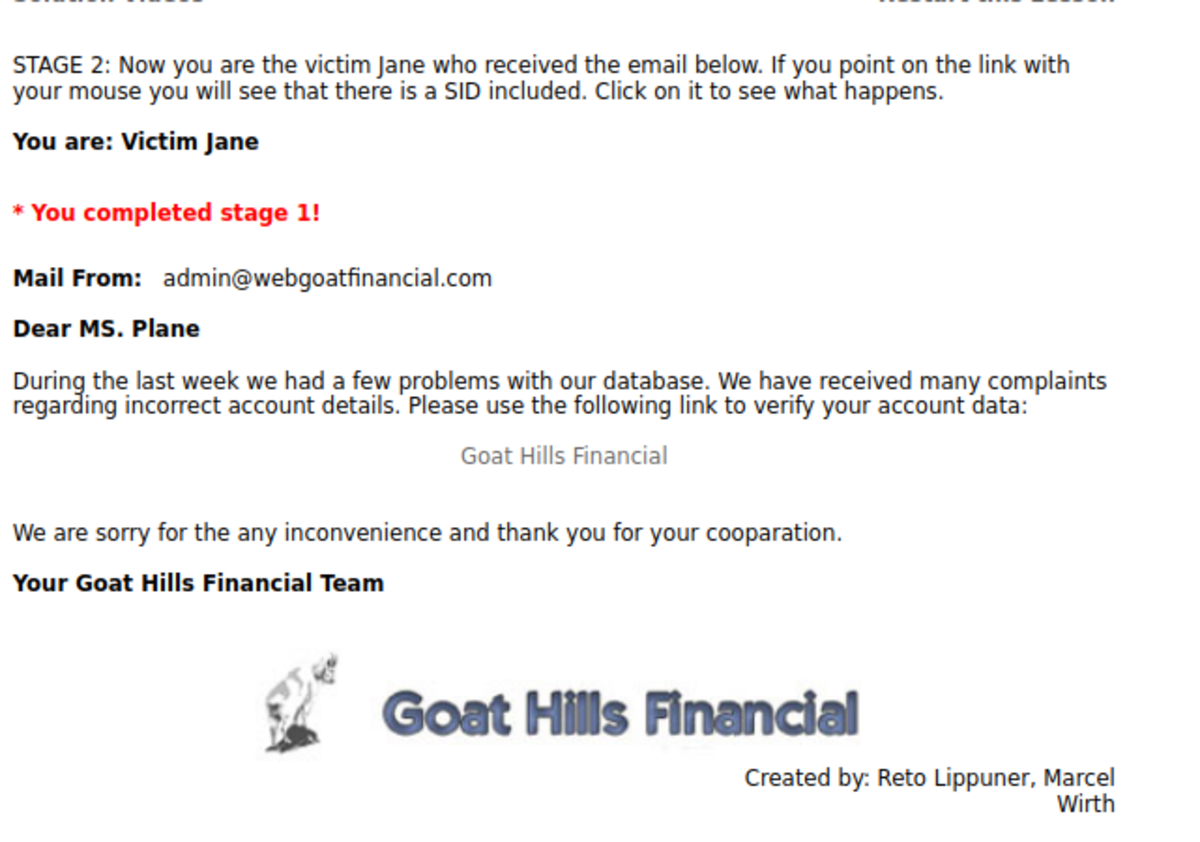
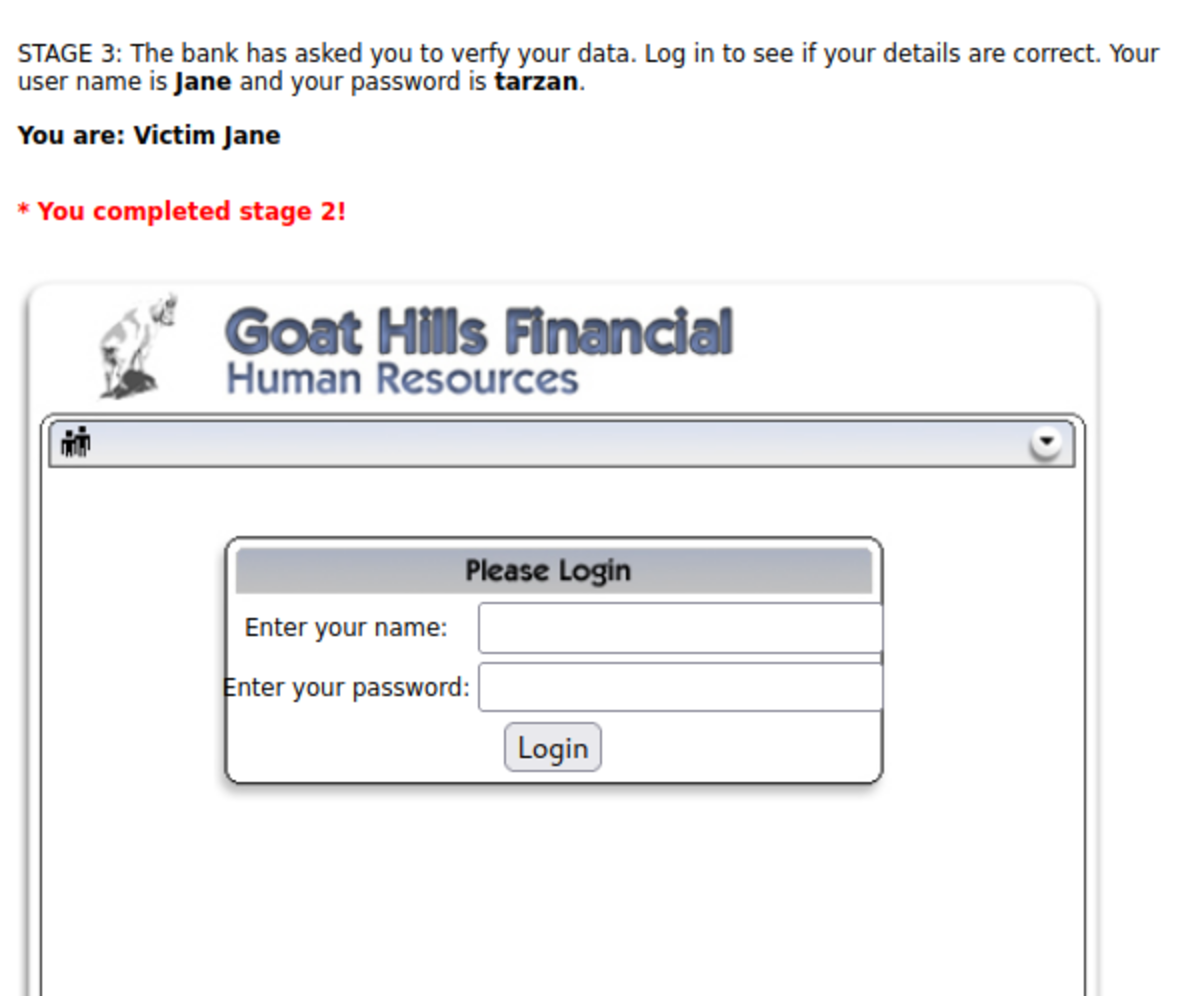
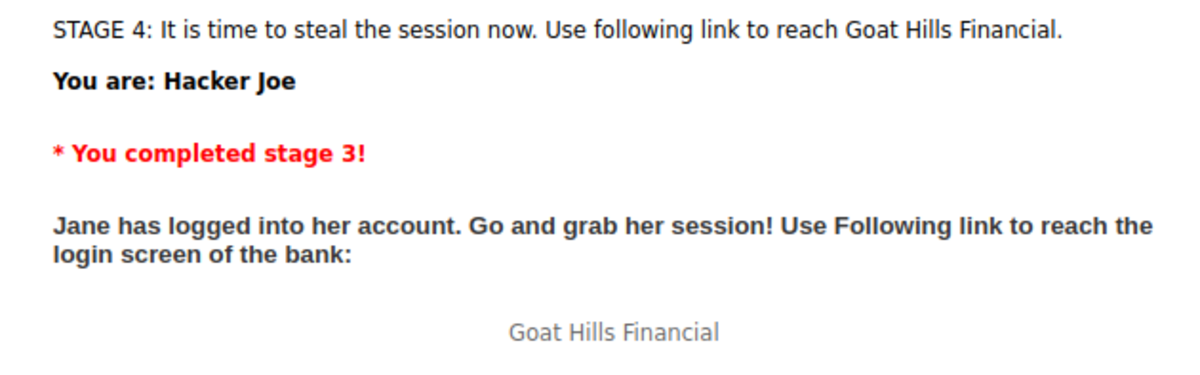
4. Session Fixation
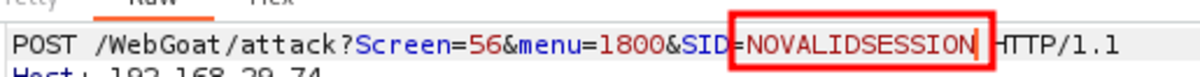
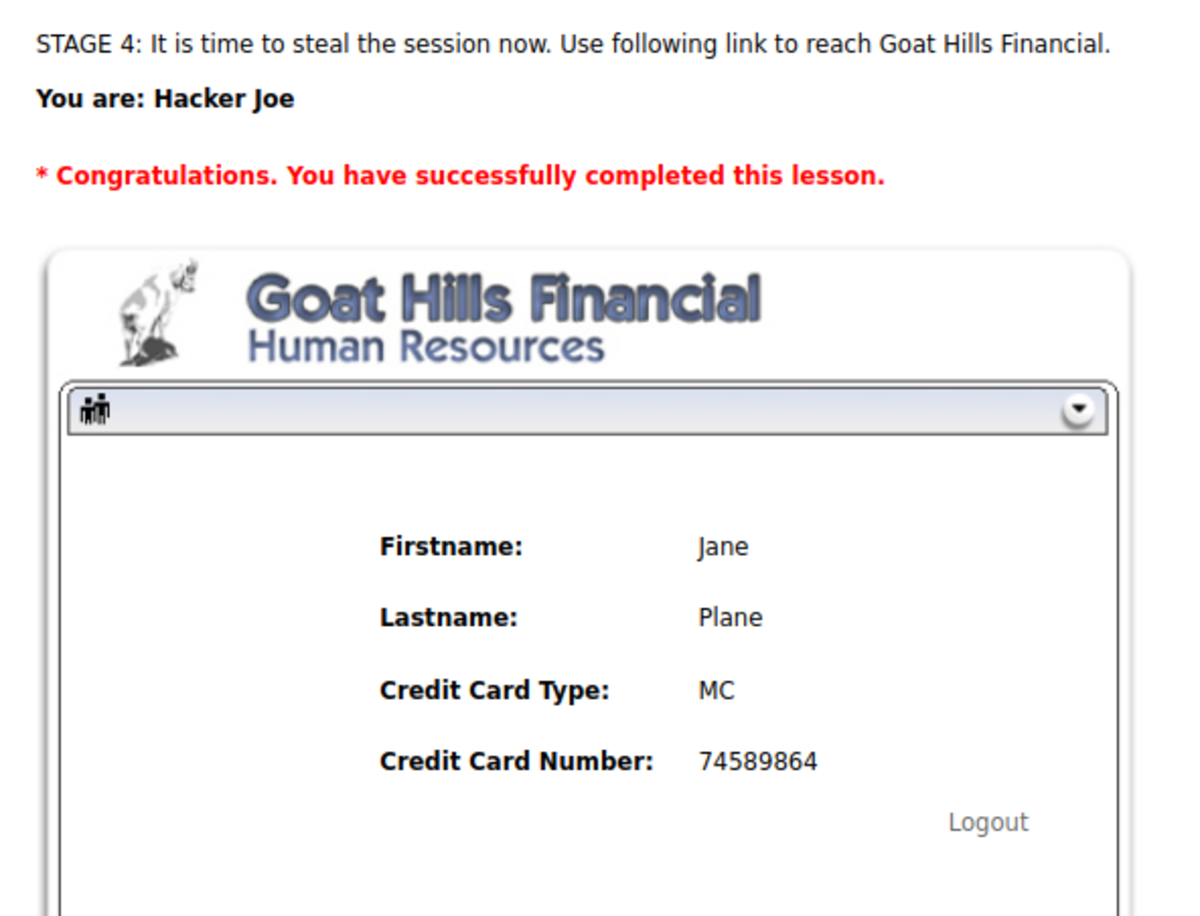
First, navigate to WebGoat and then to Note: The spelling of “webgoat” is wrong; change it to “webgoat.” Now add the session ID of your choice and send the email. Click on the link. fill in the credentials as ‘Jane’ and ‘tarzan’ Now let’s steal the session. Turn on the intercept and enter “test” and “test” as false usernames and passwords. Let’s change SID to ‘555’ that we set for the victim’s session and forward the request. Hacked !!!
How Can We Reduce its Severity?
To avoid password-guessing attacks, ensure the application enforces a strong password policy. To avoid brute force attacks, ensure that the application enforces an automatic lockout after a certain number of attempts. This would prevent an attacker from launching more brute-force attacks. Implement Multi-Factor Authentication — If a user has multiple methods of authentication, for example, using usernames and passwords and receiving a code on their mobile device, then it would be difficult for an attacker to get access to both credentials to get access to their account.
Resources
- 30+ Standard Linux Commands for Beginner or Intermediate Users
- Bug Bounty Hunting With Burp Suite (Intercept, Repeater & Intruder)
- Broken Access Control (Tryhackme and Owaspbwa)
- Html Injection (Tryhackme & Owaspbwa)
- Command Injection (Tryhackme & Owaspbwa)
- Website Enumeration and Information Gathering [Part 1] This article is accurate and true to the best of the author’s knowledge. Content is for informational or entertainment purposes only and does not substitute for personal counsel or professional advice in business, financial, legal, or technical matters. © 2022 Ashutosh Singh Patel