Topics covered:
Online Safety Strategies
The primary thing to understand about online safety is the way hackers try to get your personal information to steal your identity. You can avoid that by following a strict rule to protect your personal data. If it’s that simple, you might ask, then why are people getting malware and viruses? I’ll tell you why, and you won’t like the answer. It’s because you are allowing it! Many of the attempts by hackers are obvious, but some are well done and can fool most anyone who is not careful. And yet, if you learn to pay attention before reacting to scam attempts, you can remain 100% safe. Here are some examples:
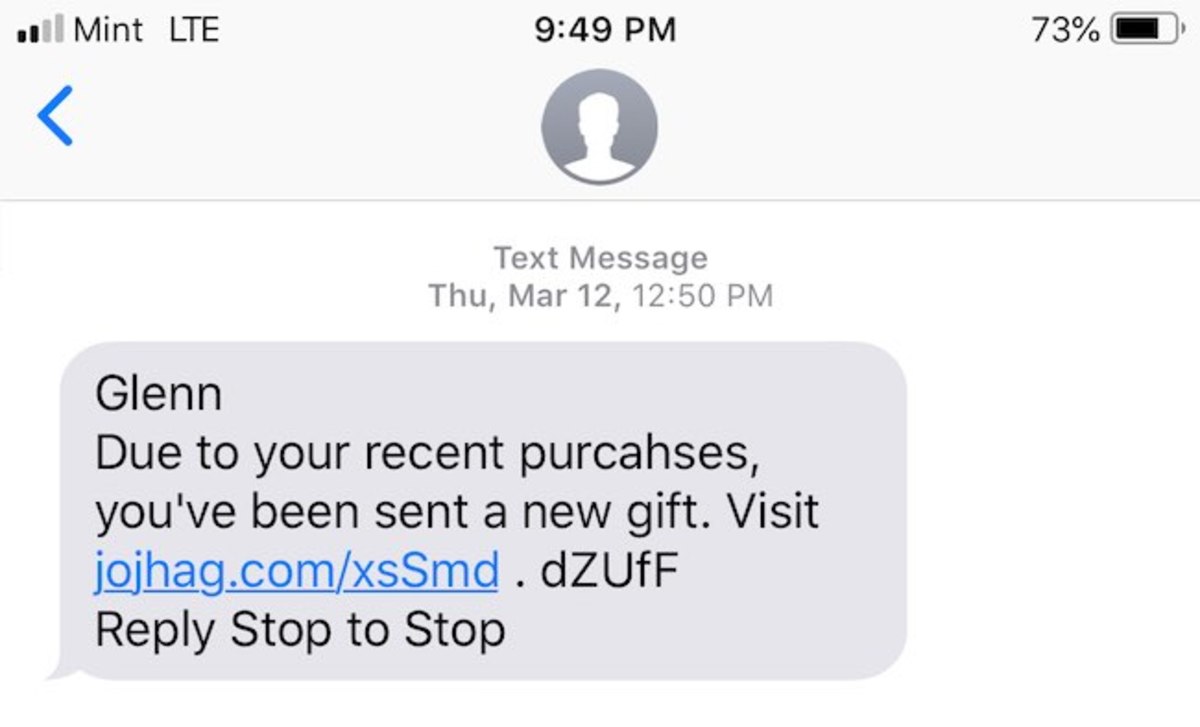
You get an email that looks as if it came from a trusted friend, asking you to open an attachment to see something interesting they want to share with you. You need to call your friend and ask if they sent that. Hackers write malware software that sends these notices to all the email addresses it finds on one’s computer. It does indeed come from a friend, but not with their knowledge. So keep that in mind. You get an email from your bank about a promotional rate offer with a link to find out more about it. Wouldn’t it be safer to call your bank directly to discuss it, if it’s even real? Never click those links. Never! You get a warning from your health insurance company telling you that a recent doctor’s bill was denied, and you need to pay the doctor directly. Click the link to make that payment or dispute the charge. Stop! Think! Did you recently even have a doctor’s appointment? If so, wouldn’t it be safer to call his or her office to confirm the notice? You get a text message offering a gift due to a recent purchase, with a link to visit, as shown in the example of one I recently received below. Just look at that link! It’s not clear where it’s going to take you. Would you click that?
Extend Your Smartphone’s Battery Life
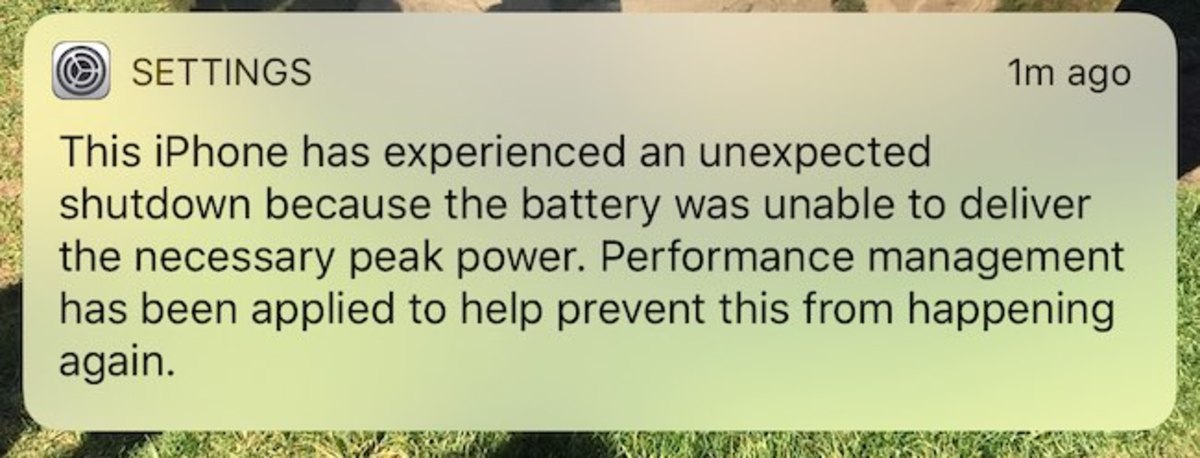
You can extend your phone’s battery life with a few simple changes. That last item might be the worst culprit. If you have apps you haven’t used for a long time, you should consider removing them. Some apps run in the background, monitoring your activity. The developer might be using that data to send you notices or advertising based on your interests. They might even sell that information to other ad agencies. Some apps will even drain your battery faster than usual. You can extend your battery life by getting rid of unnecessary apps. If you ever notice your phone getting unusually warm after you just started using a new app, get rid of that app pronto! That’s a sign that it might be doing awful things invading your privacy, such as recording your voice, your image, your location, and maybe even downloading data from other apps on your phone. Below is a real iPhone warning that shows an extreme case when an app had put way too much load on the battery.
Why Online Bill Payment Is Safe
Many banks offer online bill payment services. Did you know that these methods of paying bills are safer than writing checks? If you’re not already using these services, it’s time you catch up with the times. Checks sent through the post office can be lost. Worse, a thief can fish your mail out from a mailbox and get personal information to steal your money. A friend told me what happened to her once. She mailed a bill payment with a check, dropping it in a local mailbox. A thief fished the mail from that mailbox before the post carrier emptied it. The thief whitewashed the “pay to” and the amount, changed it to their name (a phony name with a temporary checking account), and wrote an enormous amount in the payment field. My friend had opted in for a service most banks offer that avoids bouncing checks. That authorizes the bank to accept any checks that go over the available funds. They give you a loan to cover it. Don’t ever opt into those options. My friend lost her money, owed the bank the amount with interest, and had a penalty for non-payment of the original bill. Lesson learned! She now uses online bill pay, which is guaranteed by the bank. She’ll never have to worry about non-payment, lost checks, or fraudulent activity. Most bills are paid electronically, so they clear faster, and nothing can get lost in the mail or intercepted by thieves.
How to Avoid Email Harvesting
I mentioned earlier about malware that sends an email to all addresses it finds on your computer or smartphone. You probably heard the expression that a chain is only as strong as its weakest link. Well, the weak link with emails is when someone sends an email to multiple people by placing all their addresses in the TO field. You need to avoid that practice. If any of your friends do that, you need to lecture them about the danger of sharing that information. It’s easy to prevent malware from detecting those addresses. All they need to do is place all the recipients in the BCC field. BCC means Blind Carbon Copy. CC is from the old days (before home computers) when typists used carbon paper to make copies on a typewriter. All email programs include a CC and BCC field in addition to the TO field. So start protecting your friends and associates by hiding their email addresses. The weak link would be one friend who allowed email-harvesting malware on their computer or smartphone without even knowing it, by clicking a link in a hacker’s email or text.
Keep Your Children Safe
Get to know what sites your children frequent and use parental blocking when necessary. Educate your children about Internet safety by making them aware of the risks involved. Teach them about the following dangers:
Privacy Issues With Social Media Sites
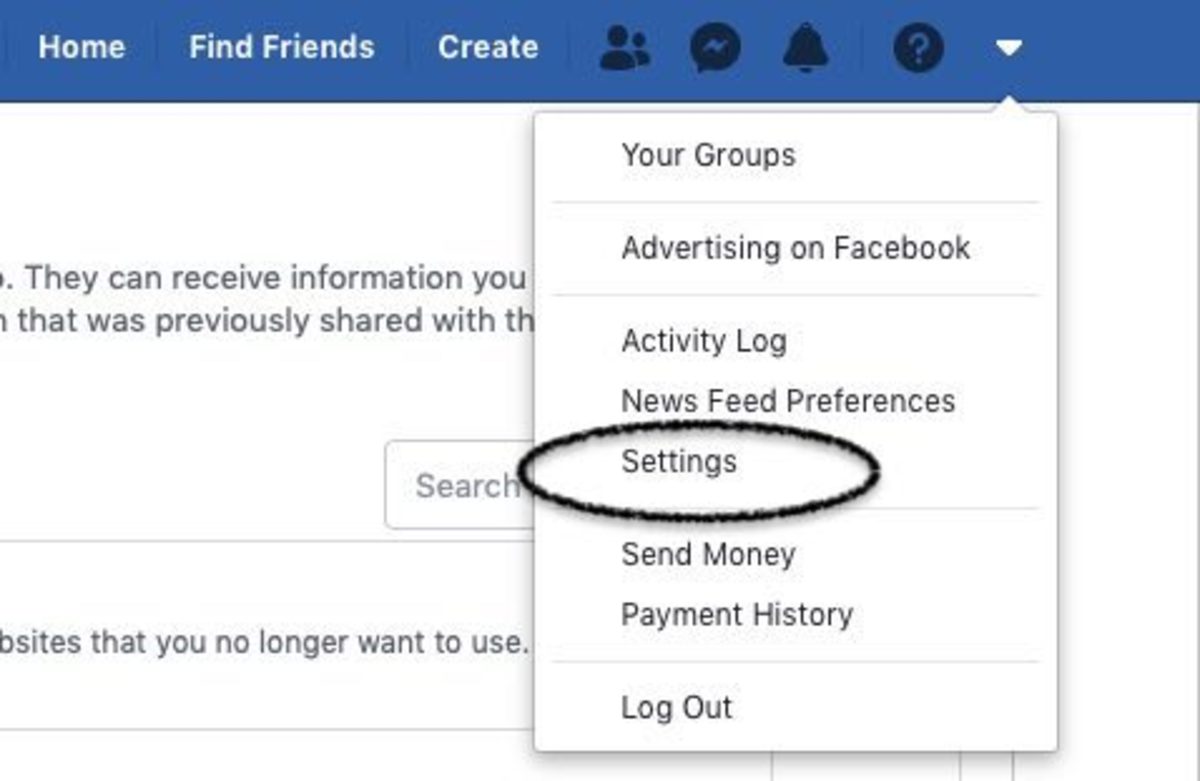
Social media is a significant part of computer life these days. People are sharing personal information on sites such as Facebook, Twitter, LinkedIn, WhatsApp, and Instagram, to name a few. How many people have actually read the privacy notice? If you ever do read all the way through, you might be too frightened ever to do anything online again. No matter what social media site you might use, you probably are sharing your other online activity. That is especially true with Google and Facebook. Both of them have activity trackers installed on most other sites on the Internet. There’s no getting away from it. That’s why you usually see ads related to your interests—no matter what site you visit. Some social media sites have personal settings where you can opt-out of permissions to share your data with third-party businesses. You should look for those options on all the social media sites you use. You can edit your privacy settings on Facebook by going to the settings menu, as shown below.
Here’s a List of Some Privacy Settings on Facebook
Who can send you friend requests Who can see your friends list Who can see your future posts Who can post on your timeline Who can see what others posted on your timeline Allow others to share your posts Who can find you by searching your email address Who can find you by using your phone number Do you want search engine lookups to link to your profile? Allow tracking your location history for your mobile devices Allow Facebook to recognize you in photos and videos by Face Recognition
Keep Your Individual Logon Accounts Separate
You may already have made this mistake. You decide to join a new social media site, and you see the option to log in by using your Facebook or Google account, as shown below this section. Don’t do it! That method gives Facebook or Google the right to track your activity and gain full access to the data you place on that account. It also lets that social media site full have access to your Facebook and Google account information. It’s safer to create a unique login account with your email and password. You may find doing that is more difficult to manage—needing to keep track of all your passwords. However, you’ll have full control over your privacy and data. That’s much more important. Get used to managing multiple passwords. It’s crucial. There is no excuse for not doing that. You can keep an off-line written ledger of passwords, or use a trusted password manager that safely stores your information encrypted so no one else can access it.
Methods of Data Backup
If you have important documents, and you’d be in trouble if they were lost, then you need to have a routine backup.
Apple
Apple computers have the best backup, in my opinion. It’s called Time Machine. It had already saved me from disaster a few times. Once when I made considerable modifications to an article that I was writing, only to realize I had deleted a section that I wanted to keep. I simply went back to the date of the version I needed with Time Machine had restored it. Another time I was cleaning up, deleting a lot of files I no longer needed. Then for another reason, I later needed one of those files. No problem, Time Machine had it saved.
Microsoft
Microsoft Windows computers have many third-party options for backup, such as Paragon and Genie Timeline. Many cloud-based backup services exist that store your data on their server, such as the well-known Carbonite. I’m not a fan of cloud backup since I’d rather keep my data locally on a private backup device that no one has access to, such as an external hard drive. But that’s a personal choice. Many cloud-based services are legitimate and will not use your data for devious activities. So if that’s your preference, just do your due diligence with researching experiences other people talk about on forum reviews.
Cybersecurity With Online Purchasing and Commerce
Online commerce is a growing trend. It makes life simpler and provides more options to find deals on merchandise. Liability does exist with the technology used for these services. You probably, by now, were already a victim of having your credit card stolen from the server of an online store. That had already happened with the likes of Sears, Kmart, Target, Home Depot, Marriott, Wendy’s, and Chipotle—as previously reported by CNET, Wired Magazine, and Fortune Magazine. Even Equifax got hacked. That means vital information about their customers may be in the hands of thieves. All these commerce sites had arranged free online monitoring for all their customers after those hacks occurred. If you do any sort of commerce online, then I recommend maintaining ongoing credit monitoring that reports to you when your personal data is found on any Dark Web sites. At the least, get a copy of your credit report once a year. All three credit-reporting agencies offer that free once a year (Equifax, Experian, and TransUnion). In addition to credit monitoring, you should enable all the reporting options on your credit cards and bank accounts. You can have a text or email alert sent to you in real-time when any of the following occurs:
When there is unusual activity found on your account When your contact information has been changed on your account When a transaction exceeds a specified amount When a cash withdrawal is made at an ATM When a card purchase occurs outside the United States When a card purchase occurs online When a new card is sent in the mail
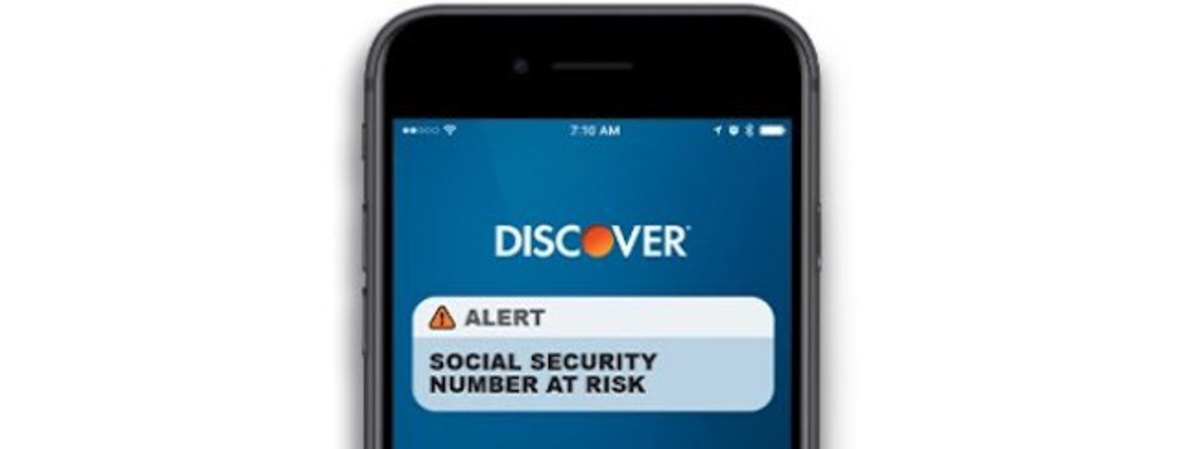
Check your bank and credit cards for any free services they provide that can help catch fraudulent activity before damage occurs. Discover Card, for example, offers free alerts when your credit or social security number has been compromised. You simply just enable that option in your account.
How Smartphone Usage Differs From a Laptop or Desktop
The obvious difference is that a desktop or laptop uses a keyboard and mouse, while a smartphone uses touch-screen technology for data entry and to control cursor positioning, scrolling, and image resizing. Smartphones have become a standard personal item that we use for most activities in our lives these days. They are quickly taking over from more traditional computers. Nevertheless, I see many issues with smartphones being challenging to manage, while a desktop computer offers simpler navigation. Some merchant and social media phone apps don’t have all the bells and whistles that their full website offers for control of client accounts. When I log in on a website I can handle things a lot easier than I can with the same company’s phone app. Some company IT programmers put more effort into the design and development of their phone apps. I hope that continues over time. For those of us who use our home computer for major tasks, such as video production, image editing, writing, and even drawing, we can’t dismiss our desktop or laptop computer. However, I find it amazing how so many tasks can be performed with a smartphone. They have truly evolved into being a necessary tool in their own right, as you’ll see with the listing I’ve compiled in the final section below.
The Multipurpose Evolution of Computers
Computers have four basic functions: data input, data processing, data output, and data storage. Ever since computers became a common household appliance, these four functions made it a multipurpose device. Home computers today, and especially smartphones, are used for an endless variety of tasks, such as:
Health monitoring Exercise rituals Telephone communication Dictation Travel coordination Digital airline tickets Digital savings coupons Supermarket delivery service Quick supermarket checkout Pizza and fast food deliveries Library book loans International trade Photography and image tools Social media Social Activities and get-togethers Online dating Scientific research Personal background research Medical diagnoses Blogging Publishing Local and remote sales Doctor and lab patient portals Business collaboration Pharmacy medication prescription updates Keeping reminders Maintaining calendar appointments Personal contact lists Banking and bill paying Stock portfolio and trading Radio and video steaming Up to date maps Driving and hiking GPS Note keeping and journaling Weather reports Web surfing Measuring distances Compass and coordinate detection Tracking walks and direction Interface with blood pressure monitors Interface with diabetes monitors Interface with health fitness gadgets Interface with garage doors Interface with doorbell cameras Interface with home security monitors Interface with vehicle performance monitors
Most of the above examples use specialized apps that run on smartphones, making our phones the most versatile instrument we have ever imagined.
To Conclude
Our use of computers will continue to be applied to more phases of our lives. For that reason, it’s imperative that everyone attempts to become computer savvy. I’ve given you the proper information to set you on the right track, and you’ve proven you can do it because you made it all the way through this article. © 2020 Glenn Stok
Comments
Mpho F on May 08, 2020: Great and enlightening piece Glenn , you opened my eyes to so much and i fully appreciate your efforts . I am more tech wiser now and enabled to make right choices from here onwards. Pamela Oglesby from Sunny Florida on April 24, 2020: This is an excellent article with a wealth of great information concerning our computers. I appreciate this information, Glenn. I definitely learned a few things from your aticle. Jo Miller from Tennessee on April 13, 2020: Some good information here. I’m bookmarking for later use. Liz Westwood from UK on April 08, 2020: As we are all turning to online activities increasingly during lockdown, this is a very appropriate and useful article. Dora Weithers from The Caribbean on April 07, 2020: Thank you Glen, for these warnings on maintaining our privacy and safety online. I prefer the computer too. My fingers stray too often on the phone and the touch is sometime too sensitive. Anyway, I learned a few things I can implement. I looked up Time Machine. Glenn Stok (author) from Long Island, NY on April 06, 2020: John Hansen - Thanks for that relevant comment John. I do many things on my desktop that the iPhone could never come close to achieving. Even though the growth of phone apps is progressing, I agree with you that a big screen and keyboard will remain necessary for major tasks, as I alluded to in this article. John Hansen from Australia (Gondwana Land) on April 06, 2020: Good article Glenn, and very helpful for those not completely computer or smartphone savvy. For me the smartphone will never take over from the computer though. I prefer a big screen and regular keyboard and find everything difficult to navigate on a phone, hence I only use the Internet on it in emergencies. As you said most apps don’t give you the full functionality of the website either.