Shutterstock There are hackers and criminals who can attack your computer. They can run up charges on your credit card. They can even steal your identity, drain your bank account and open up credit accounts in your name. In the United States, a computer is hacked, on average, every two seconds. The estimated cost of computer attacks on U.S. households is $4.5 billion per year. But if you learn to take a few simple precautions, you can feel safe exploring the highways and byways of the World Wide Web.
Staying Safe
In this article, I’m going to teach you what you need to know to be safe on the Internet. It’s a long article, but you will learn a lot! You’ll learn how to secure your computer against hackers and malware. How to avoid information phishing in email and on the web. How to protect private information on your smartphone and tablets. Let’s start with computer malware.
What Is Malware?
By malware, I mean any software that is intended to harm your computer in some way. There are several types of malware:
Malicious malware is just intended to do harm. It may delete important files, output offensive messages to your display, or play other pranks. Malicious malware is just vandalism, pure and simple. Adware pops up ads on your computer display Sometimes it’s tied to a particular web browser, and sometimes the ads will pop up in other programs. Spyware searches your computer for sensitive information, like bank account numbers and passwords, and sends it back to the hackers who are spying on you. Hijackers use your computer for their own purposes. Once the malware infects your computer, it may be used to send SPAM email, or distribute illegal files… even things like child pornography. Ransomeware literally locks up or disables your computer. You can’t use the computer unless you pay the hackers for a code to unlock it.
There are two different approaches that hackers use to get malware onto your system: viruses and trojans. It’s important to understand that, whether the malware arrives as a virus, or as a trojan, it can still do all the bad things I mentioned. That’s why you need to guard against both approaches!
Viruses
Viruses are programs that exploit vulnerabilities on your system—just as human viruses exploit weaknesses in your immune system. They find holes in your computer’s defenses, and slip in through those holes. One virus, called the “Conficker Virus,” infected over nine million computers! To defend against viruses, you need to be sure your computer has strong defenses, and that you keep them up to date.
Trojans
Trojans use a very different strategy. Remember the story of the Trojan Horse? The Greeks built a huge wooden horse, and they left it outside the gates of Troy as they sailed away. The Trojans thought the horse was a gift, so they hauled it inside their city walls. Then during the night, the horse opened up and a bunch of Greek soldiers slipped out and killed the Trojans. Trojan programs use the same kind of trick. You may find a website that offers you a free game. Or maybe a website will say that you need to update Flash on your computer. But when you download and software and install it, you are really installing malware. Trojans can also arrive as email attachments, which install malicious software when you open them. Hackers trick you to get past your computer defenses, just like the Greeks tricked the Trojans.
Protecting Your Computer
The best defense against both viruses and trojans is up-to-date software. Modern computers—both Windows and Macintosh—have good defenses to recognize and block malware. But the bad guys that create malware keep getting smarter. It’s very important that you regularly install updates to your computer, to block the newest attacks. As an extra layer of protection, you should also install a malware protection program (also called an anti-virus program). I recommend Bitdefender. A one-year subscription costs under $50, and it can be installed on up to five computers. If you’re looking for a free option, consider Malwarebytes, which can be downloaded directly from the company’s website. Whatever option you choose, it’s important to install updates as they become available! We’re not done securing your computer yet! In medieval times, castles had layers of defenses, one wall within another. One of the main defenses was the Castle Gate. So let’s put a lock on our castle gate! That means putting a login password on your computer. You may not think this is important if only you and your family have access, but there may be times when there is a repairman or casual acquaintance in your home. It only takes a moment to install a spyware program on your computer if it’s not protected by a password. Also, if your computer is ever stolen, a password may keep the thief from accessing your personal information. The FBI estimates that two million laptops are lost or stolen every year!
Backups: The Final Defense
Besides the things I’ve already talked about, like installing an anti-virus program, and keeping your software up to date, I recommend performing regular backups. A backup is the “last defense” against malware. If a virus gets past your defenses and damages your files, you can recover them from a recent backup. And if a new virus attacks your system, and your anti-malware programs can’t remove it, you can restore a backup from before the virus appeared. Of course, it’s always a good idea to have a backup in the event of a disk failure. And that happens much more frequently than you may think. To backup your system, you’ll need an external disk drive. You’ll also need to get backup software, if it does not come with your disk. I recommend Acronis True Image for Windows, and Carbon Copy Cloner for Macintosh. How frequently should you run a backup? That depends on how much you use your computer and how many files you change. Think about this: how much work would you be willing to lose if your hard disk fails? Some backup software has the option of copying only files that have changed since the last backup. This can really speed up your regular backup routine. I recommend backing up a least once a week, and more frequently if you’re very active on your computer. Mark it on your calendar and be sure to run those backups!
Securing Your Network
Even if your computer is well defended, hackers can gain access to your important information by accessing your home computer network. So let’s take a few minutes to make sure it is secure as well. You’ll need to consult the documentation for your wireless router in order to configure it properly. The router may be built into your cable modem, or it might be a separate box that attaches to the cable modem. The manual will tell you how to log in to your router control panel from a browser window on your computer. If you don’t have the manual, look on the bottom or back of your Wi-Fi router for a model number. You can then do a web search for a manual for that router make and model. Once you log in to the router, you’ll see a menu with lots of selections. Your router admin page may look very different from this example. You’ll need to look at each menu option until you find the following settings:
Change the Admin Password. Most wireless routers come with a really weak login password… usually “admin” or “password.” So the first thing you want to do is change that to a strong password. Change the Network Name. Find the Network Name (also called the SSID) and change it from the default. Others can see this name when they scan for Wi-Fi connections, so use something that won’t disclose your identity. For example, don’t use your name or address. A good principle is to never give hackers any information that may help them. Set the Security Protocol. Find the security options or security protocol, and set it to WPA2. That’s currently the strongest security. If your router doesn’t support WPA2, use WPA. Change the Passphrase. Finally, you’ll need to enter a passphrase, also called a security key. That’s the phrase you’ll need to type the first time you connect your computer or other device to your Wi-Fi network. It’s really important to choose a strong passphrase, and it should not be the same as the admin password. Be sure you write this down and store it, but don’t leave it in an obvious place!
That’s it. Save your settings, and close the router admin screen. Note that, because you changed the passphrase, you’ll need to reconnect your computer to the network. Your computer should prompt you for the new passphrase.
The Biggest Risk: You
I’ve talked about making your computer and your network more secure. Now it’s time to talk about the biggest risk factor online… the person behind the keyboard. Even the best software can’t protect a computer from a user who does dumb things. Fixing this problem is hard, because it requires changes in behavior. The good news is that the rules are pretty simple: To help understand these rules—and how they apply to your day-to-day activities—I’ll go through a few specific examples.
Suppose you get an email from your friend Sue. It says, “Could you please review the attached spreadsheet?” What should you do? The email may be a legitimate request from Sue, so if you throw it away you won’t get the file she wanted you to review. On the other hand, it may have been sent by a hacker who forged Sue’s “from” address. It may even have been sent by a virus on Sue’s computer! The attachment may be a trojan, and opening it could infect your computer. Your anti-malware program might prevent the infection, but why take chances? The best course is to simply contact Sue before you open the attachment. Now suppose you get an email from a friend saying he was robbed while vacationing; you need to wire money so he can get home. The email is very convincing and even includes personal details about your friend. What should you do? Of course, the correct answer is (2). Never click or send anything—especially money—based on an email alone! Scams like this are very, very common. Old-fashioned con artists have learned to use the email to find new victims. They can get all sorts of personal info from social media, and they use this information to make their appeals more convincing. Con artists are good at making their scams seem plausible, even attractive. They may offer to send you money (in the form of a bad check), or give you a great deal on something, like free tickets to your favorite band (after checking out your Facebook page). The mail may even look like it was sent by a friend. Con artists have gotten very good at what they do, and they can even fool security experts. (See my article I Almost Fell for a Sophisticated Phone Scam.)
Phishing
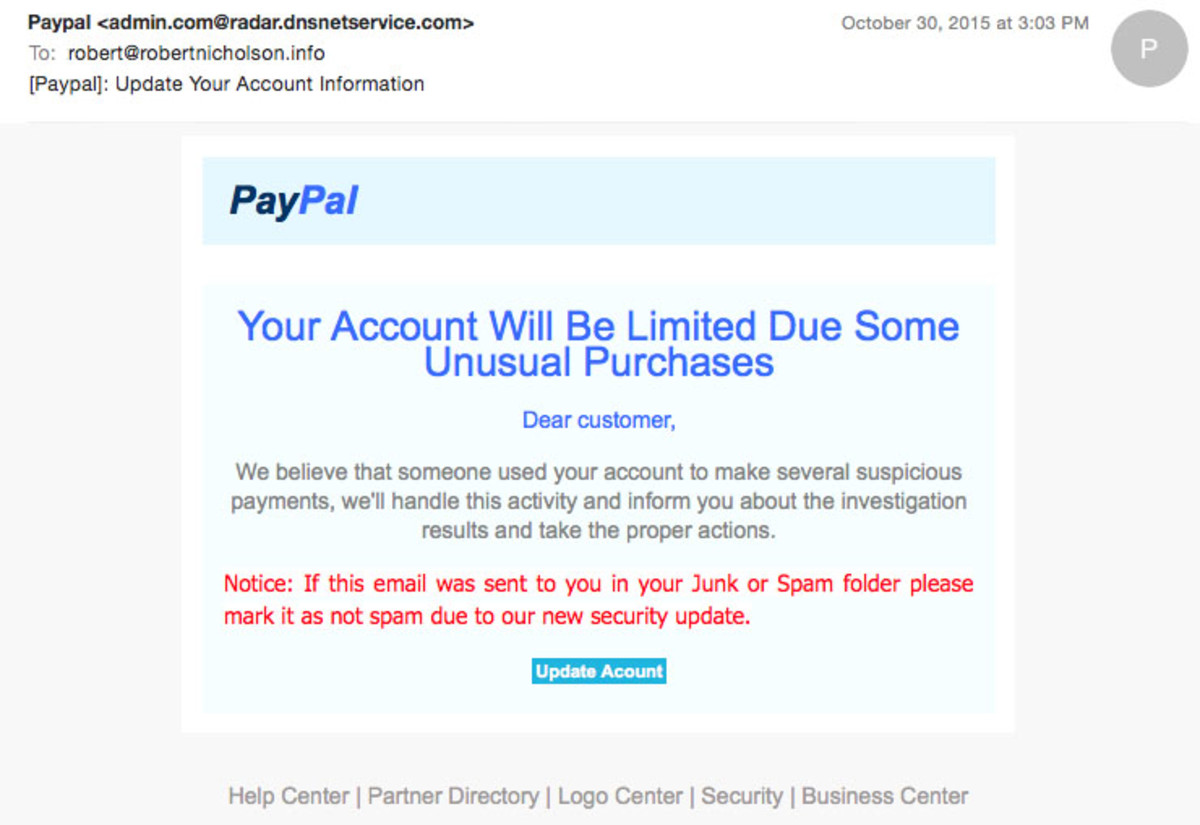
Now suppose you get an email from your bank saying there is a suspicious charge on your credit card. There’s a link to log in and verify the charge. What should you do? The email may be legitimate, so don’t throw it out. But don’t click the link in the email! It might take you to a phony site. When you try to log in to the fake site, the hacker will have the login info for your bank account! Trying to trick people into giving up private information like passwords is called phishing (with a ph). A few years ago, phishing attempts were very crude. The fake sites were obvious. But now the criminals have gotten very, very good, and the email and websites can be quite convincing. So instead of trying to figure out if the link is legitimate, go directly to the bank site by typing its address, or using a bookmark if you have one. Or you can get the customer service number for the bank and phone. Don’t use a phone number from the email—that could be fake too! Let’s look at a real phishing email, and talk about some fo the clues that may tip your off. We can learn quite a few interesting things from this email.
From address: There is an important clue that this email is not really from PayPal—the “from” address is from someplace called dnsnetservsce.com. But even if the From address was paypal.com, I still wouldn’t trust this message because the From: address can be forged. Logo and images: The logo in this message looks good, but often the logo in a phishing message will be blurry, or even an old, outdated version! Headline: Phishing attacks often start with a scary message to trick you into taking action without thinking. This email asks me to click a button to update my account. Instead of doing that, I could go log in to my Paypal account directly to see if there are any messages. I could even call PayPal customer support. (Note that if there is a phone number in the e-mail, you can’t trust that either… get the customer support number directly from the Paypal website!) Greeting: The Dear Customer greeting is suspicious. A real message from PayPal would probably address you by name. Content. The awkward grammar in the content is another good indication that the email is a fraud. Button. A button or link can direct you to a phony site designed to steal your information. Instead of clicking the button, always go directly to the company’s website, by typing their address into your browser.
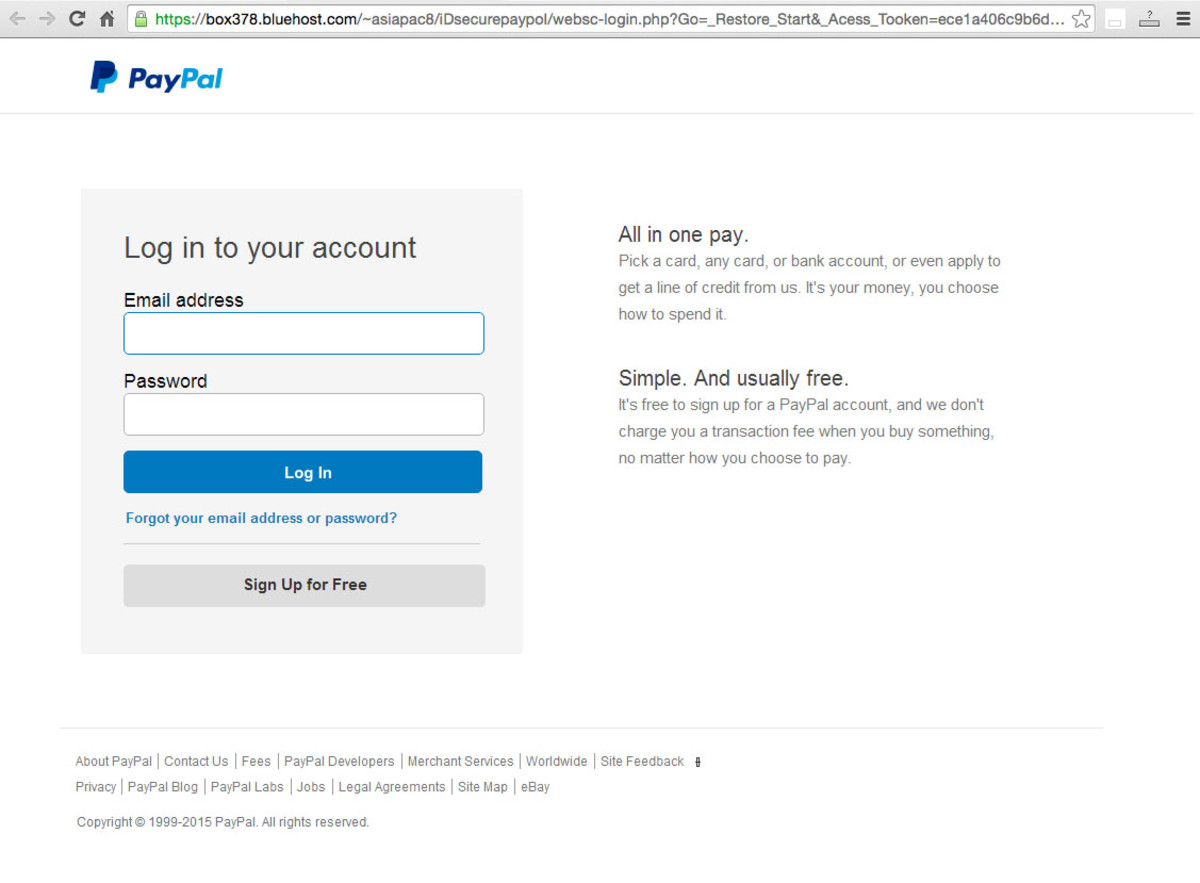
Remember, scammers are getting much better… so don’t rely on clues like these. Even if the email looks perfect, don’t trust it! I actually got this email while working on a computer security course, so I decided to explore a little further. Since I have a very secure system, I clicked the button in the email, and it took me to the web page below. Don’t do this at home, for reasons I will discuss shortly. Never click links in a phishing email! This page looks very convincing. It may have been copied from a real PayPal page. But in this case, the give-away is in the browser address bar. The address is not at PayPal.com. Instead, it’s at Bluehost.com, a commercial hosting service where the hackers have set up an account. (Incidentally, immediately after taking this screen snapshot, I contacted BlueHost.com, a web hosting service, and had their security team shut down this hacker’s account.) The address isn’t always so obvious. Sometimes scammers will use an address like paypalaccounting.com, or paypalsupport.com. Don’t be fooled! If I went ahead and tried to log in, I’d be sending my Paypal login information directly to a hacker, who could use it to access my real Paypal account.
Safe Email Practices
So let’s summarize the rules for protecting yourself from phony emails: And just like your computer and your network, your email account should have a strong password, to prevent hackers from gaining unauthorized access.
Safe Internet Browsing
There are a lot of ways to get into trouble on the Internet.
Phishing sites can try to scam you into giving them personal information. Software that you download may be infected with viruses. It’s even possible for your computer can become infected with a virus just by visiting a malicious website!
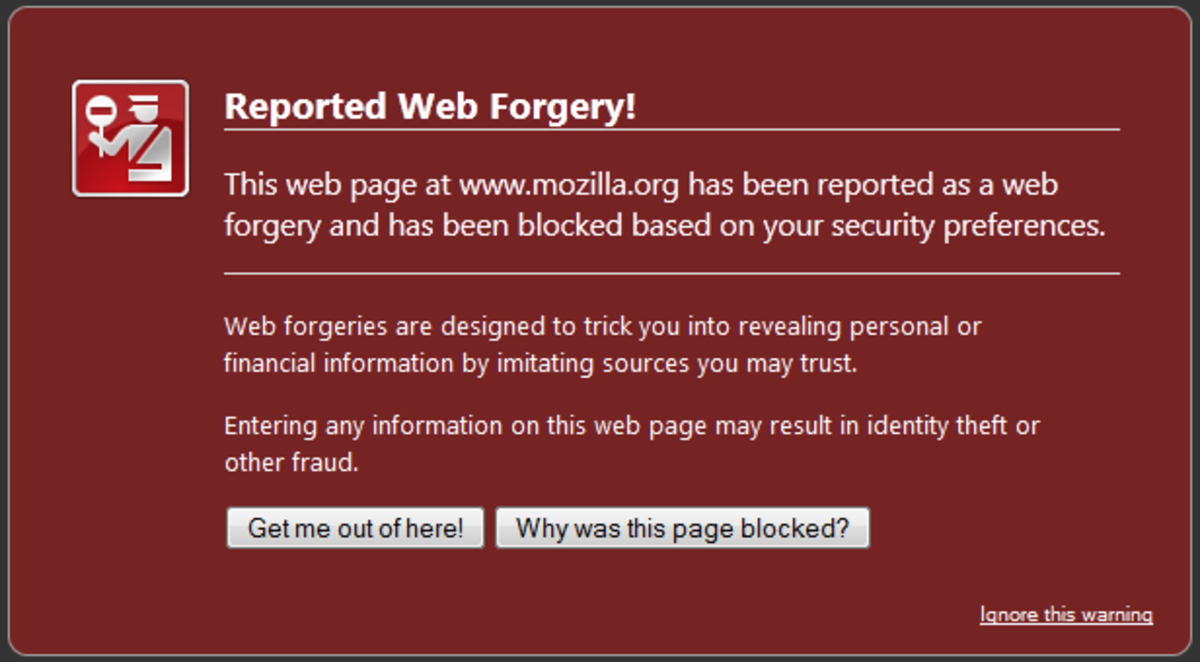
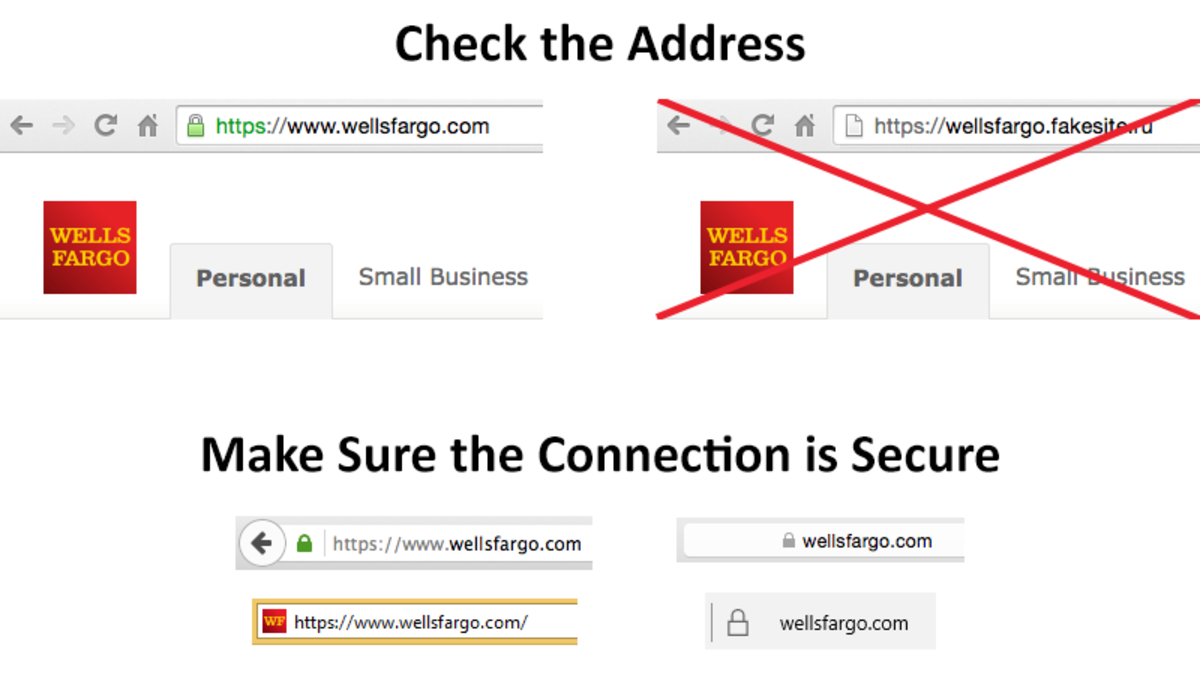
The built-in security software on your computer, and extra antivirus software that you install, does a good job of protecting you, but hackers keep coming up with new ways to get around the defenses, so you are never completely safe. That’s why you need to follow safe browsing practices. Your browser may warn you of malicious websites. If you see a warning like the one above, leave the site immediately! Of course, you can’t depend on warnings. A site may have malware that hasn’t been detected by the browser. So you should try to avoid bad neighborhoods on the web. Some sites are more likely than others to be spread malware. In general you should avoid pirate movie or music sharing sites, offshore prescription drug sites, link farms, or other sites that promote questionable activities. Some of these sites are perfectly safe, but they are often used to spread malware. If you must visit a suspicious site, you should run a malware scan immediately afterwards. And remember, don’t click on links in phishing emails, which can also take you to malware-infected sites. Be extra careful when you’re entering sensitive information on a website. We saw an example early of a phishing site that was set up to steal your Paypal login information. To prevent phishing attacks, check the address to be sure you’re on the right website, especially if you followed a link to get there. Also, make sure you have a secure connection. There are two types of internet connections—the original http connection, and a secure connection called https. Don’t submit sensitive information, like your credit card number or social security number, unless there is a secure connection. Browsers indicate this in different ways, and unfortunately the graphics change in each release. Be sure you see the small lock icon, or address starts with https. If the connection is not secure, then hackers could intercept your information as it travels over the Internet.
Avoid Downloading Trojans
When you download files from the web, you risk downloading a Trojan—a program that includes hidden malware. It’s best to stick to major websites from well-established companies. It’s really important to avoid downloading from pirate sites. Studies have shown that over 40% of the files on these sites contain malware.
Protect Your Privacy
When I talk about staying safe on the Internet, people usually ask me about privacy. Privacy is an important issue, but it means different things to different people. Also, the issue goes way beyond the Internet. For example, I can buy a database that will tell me whether you belong to a golf club or a tennis club, what kind of car you drive, what magazines you subscribe to, and even your political leanings. Marketers use this information to decide what sort of ads to send you. This information has been available for a long time, and short of going off the grid and living in a cabin in the woods, there is nothing you can do about it. But the Internet adds a few more wrinkles. Websites may share their information. So even if you give only a little information to each site, soon all of the sites may have all of your information. Now most sites have preferences and settings so you can control how much of your information gets shared. But they keep changing the rules and the settings, so it’s very, very hard to control who gets to see your information over time. Websites also use cookies—small bits of information that are stored in your browser—to track your activities on the Internet. So if you search for information on Florida vacations, you will start seeing ads for Florida timeshares, hotels, and even airline flights on other sites. All of this is a little creepy, but in my experience it’s mostly harmless. If it bothers you, I’ll give you a few suggestions for dealing with it.
Privacy Settings
One way to protect your privacy is to control who sees what on social networks like Facebook, Twitter, and LinkedIn. Each social network has privacy settings that you can control, like this example from Facebook. Unfortunately, the settings and controls are different for each social network, and they even change from time to time. So unless you want “everyone in the world” to see what you’re posting, you should spend some time learning about the privacy settings on each network that you use.
Cookies
I mentioned earlier that advertisers and websites often share information about you, to do things like better targeting ads. This is usually done through the use of cookies, or small bits of information that websites store in your browser, so they can keep track of you. You can limit, but not prevent this, by going to your browser preferences and turning off cookies. I don’t recommend this however, because many websites require cookies in order to operate properly. Note that Google, the world’s largest ad network, allows you to turn off ad tracking—at least for Google ads.
Be Careful What You Share
Some kinds of information require more caution than others. Here are some guidelines on how you should share your information:
Using Public Wi-Fi
You may remember that I talked about securing your home Wi-Fi network. When you’re using a public Wi-Fi network, you have no way of knowing if it has been properly configured—it may have been hacked. Also, it is theoretically possible to intercept Wi-Fi traffic—even secure communications. This would require an extremely sophisticated hacker, and I don’t know of any cases where this has actually been done. But just in case, you should avoid sending sensitive information over a public Wi-Fi network. In other words, don’t log in to your bank while you’re sitting at Starbucks!
Cloud Services
Many people these days use cloud services to store and share information. Remember that anything you upload to “the cloud” is actually stored somewhere on a server. If that server is hacked, then all of your information can be stolen. So feel free to use the cloud for your photos, music, and even projects you are working on—but don’t store sensitive information on your cloud account! (I work for several corporate clients who prohibit employees and contractors from using cloud storage for company information.)
Securing Your Phone
Keeping phones secure is very important, because they pose some special security risks. Your phone may store credit card information that can be used to make online purchases or other charges. It probably has full contact information for your friends, business colleagues, and acquaintances. The phone itself poses a risk. Malware programs can place calls to pay-per-minute “900” numbers without your knowledge. These risks are even greater than they might be on your computer, because your phone is a mobile device that is easily lost or stolen. The most basic way to protect your data is to lock your phone, so that a PIN code or password is required to use it. Otherwise, if your phone is lost or stolen, the person who has your phone will also have access to all your personal information. It’s also important to install software updates as soon as they are available. Just as with software on computers, the updates fix problems that hackers may exploit.
What to Do If Your Phone Is Lost or Stolen
It would be great if there was a simple way to find a lost phone, and possibly recover a stolen phone. And there is! Each of the major phones has a built-in app that can do several things:
Play a sound, to help you find the phone if it’s nearby Locate the phone on a map (using another computer or phone) Remotely lock or erase the phone if you are sure it has been stolen.
However, in order to use these services, you’ll need to have an online account linked to your phone. For Apple iOS, be sure you set up an Apple ID on your phone; for Android you will need a Google account, and for Microsoft you’ll need a Microsoft account. You’ll need to set this up on your phone before it is missing. Eventually you will want to sell or give away your phone. Before you do that, you should backup your data, or transfer it to a new phone, and then erase the phone and restore it to “factory settings.” Check your phone manufacturer’s website to learn how to enable these features.
Be Careful Installing Apps
Applications that you download from Apple’s App Store or Google’s Play Store are prescreened for malware. The screening is not perfect… malicious apps have slipped by both Apple and Google. Apple does not allow iPhone apps to be downloaded from any other source, while Android can download and install apps from third-party websites. I advise not doing this, unless the app is coming directly from a major company website. Android phone manufacturers often add bundled apps that are not screened by Google, and some of these apps have been found to contain malware. It’s a good idea to simply delete any apps that have been added by the phone manufacturer. A study done by Nokia in 2019, found that Android devices were 50 times as likely to have malware as Apple devices. The best way for Android users to protect themselves is to download apps only from the Google Play Store.
Conclusion
The Internet can be a dangerous place, you need to be smart and careful. If you take the precautions outlined in this article, and develop good habits, you can stay safe on the Internet. This content is accurate and true to the best of the author’s knowledge and is not meant to substitute for formal and individualized advice from a qualified professional. © 2020 Robert Nicholson
Comments
Michael Coulter on March 30, 2020: I used Acronis for many years but abandoned it when I had recovery problems because it depends on Microsoft services. I now use Macrium Reflect and am happy with it. Liz Westwood from UK on March 30, 2020: This is an extremely useful article and one which deserves bookmarking for future reference. I really appreciate the easy to read and navigate structure, as well as the attention to detail.