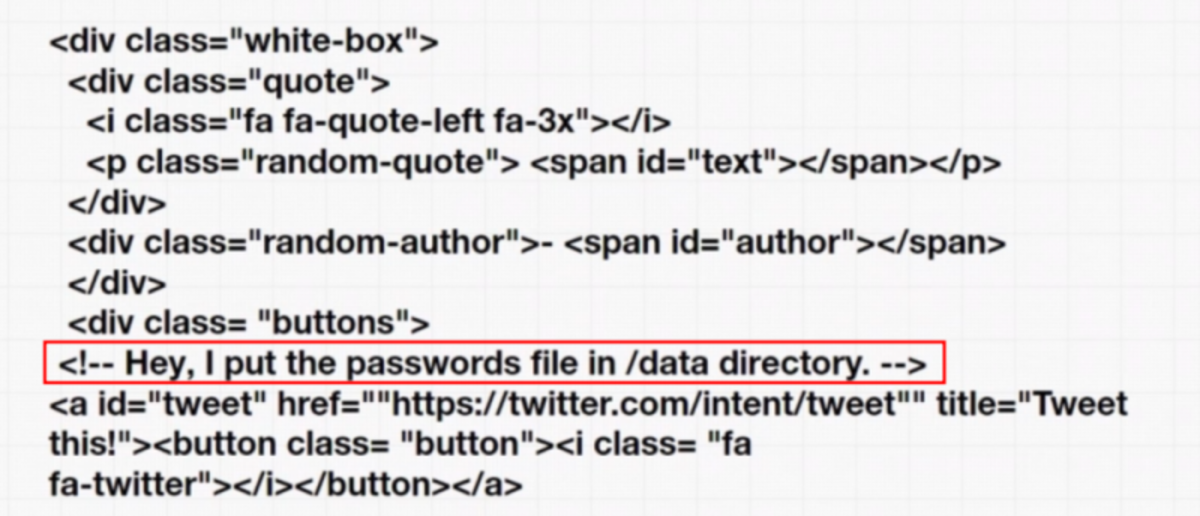
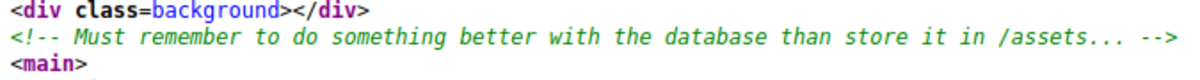
The vulnerability that developers make by exposing some unwanted information on the webpage. It might be as trivial as showing the application version to be something as big as exposing the entire database in the web application. Usually, the data will be exposed in the source code itself from the web page.
(It’s probably a general comment that the developer forgot to remove before deploying it. Or in the worst case it might be a honeypot to catch the hackers)
TryHackMe (OWASP TOP 10 [Task 11])
If this is your first time working on TryHackMe and you don’t know how to set it up then, check out the bonus resource section at the end. Navigate to: https://tryhackme.com/room/owasptop10 → Task 11
Under the Login page source code
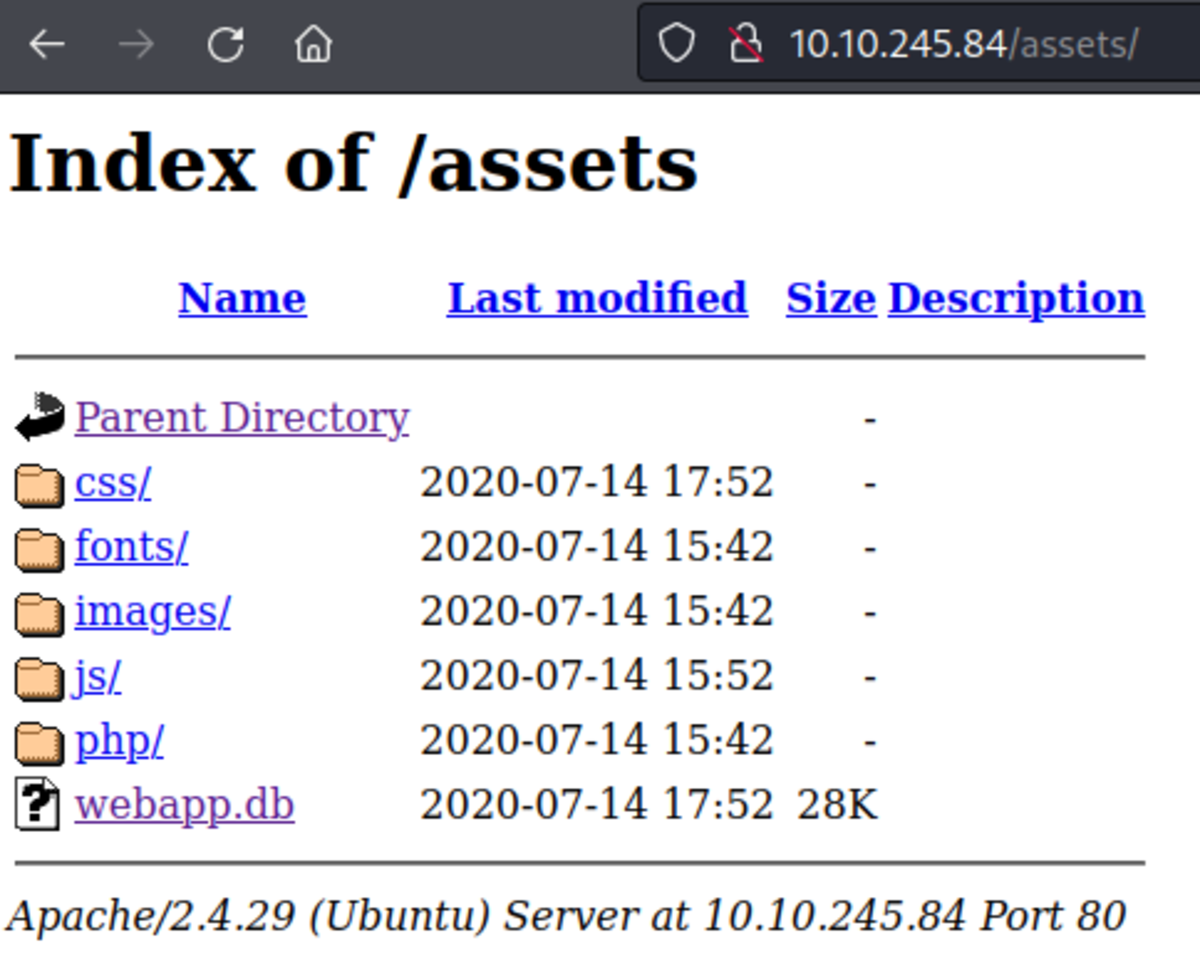
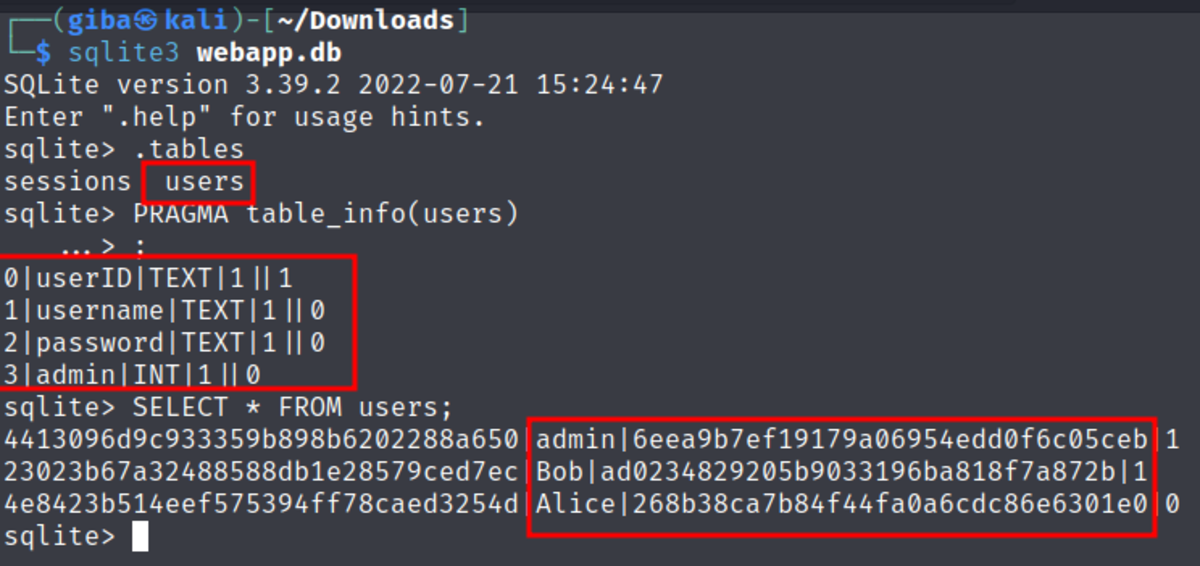
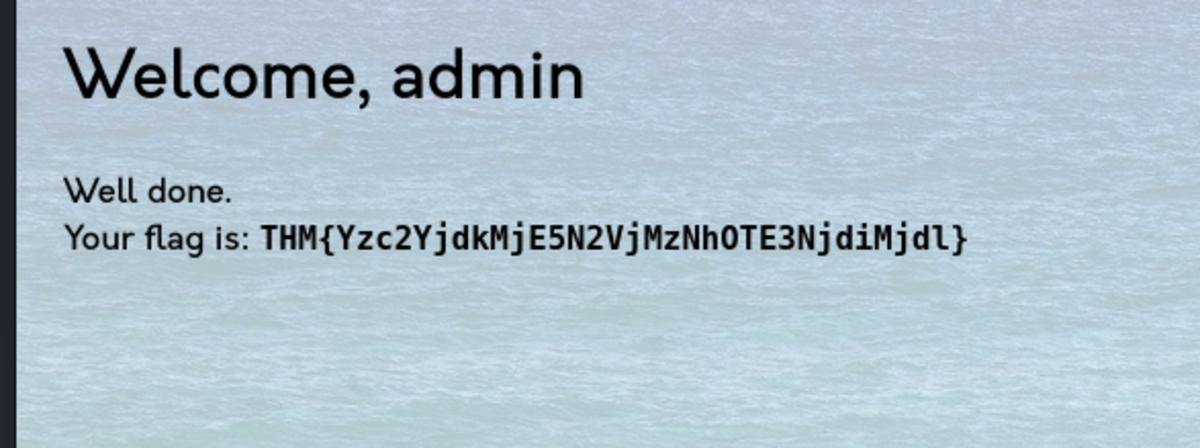
Download webapp.db Let’s crack the password for username ‘admin’ Now head on to https://crackstation.net/
Resources
- 30+ Standard Linux Commands for Beginner or Intermediate Users
- Bug Bounty Hunting With Burp Suite (Intercept, Repeater & Intruder)
- Broken Access Control (Tryhackme and Owaspbwa)
- Html Injection (Tryhackme & Owaspbwa)
- Command Injection (Tryhackme & Owaspbwa)
- Website Enumeration and Information Gathering [Part 1] This article is accurate and true to the best of the author’s knowledge. Content is for informational or entertainment purposes only and does not substitute for personal counsel or professional advice in business, financial, legal, or technical matters. © 2022 Ashutosh Singh Patel