Why Do We Do It?
We want to learn as much as we can about our target before we perform any type of attack. We want to know what we are dealing with and what the structure behind the website looks like. Does it have forms we can attack? Where is it located? What is the website used for? Is there any information about the website that could be useful for us?
What to Look for on a Website
IP addresses using tools like Nslookup, and host. Technical info on IP address after putting it in a scanner. Like open ports and services running on those open ports. Website structure (What is the website made of? Does it have js? or PHP ? or any third-party application running?) Login page/registration forms Type of server the website is hosted on Type of OS hosting the website Does the server have some other ports open besides the ports that are used to host the website? Get information from a database that it shouldn’t give us such as other users’ passwords. Check if the site has good encryption, maybe it has weak encryption or no encryption which can be exploited through a man-in-the-middle attack that could capture the passwords as plain text.
Techniques + Tools
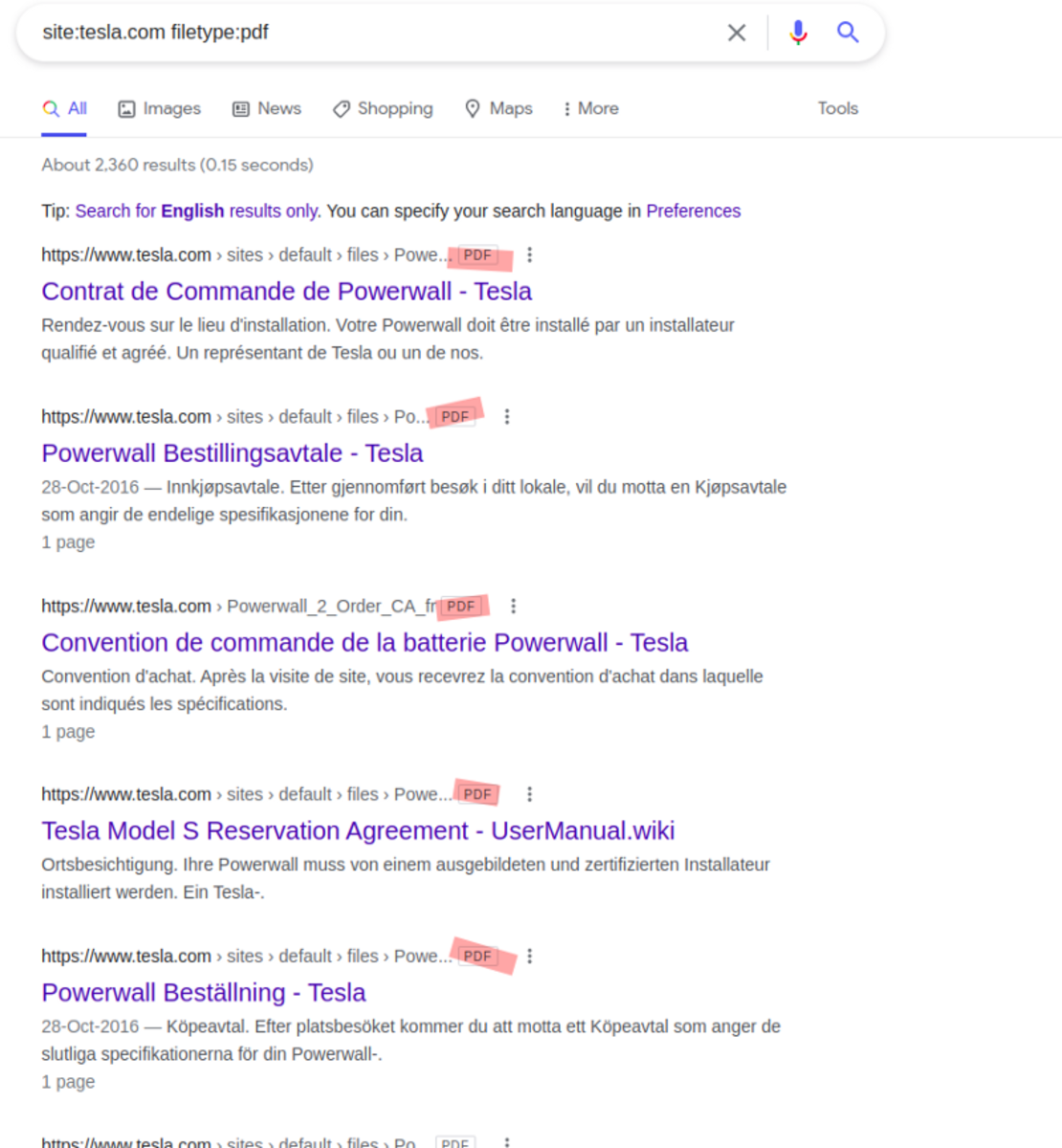
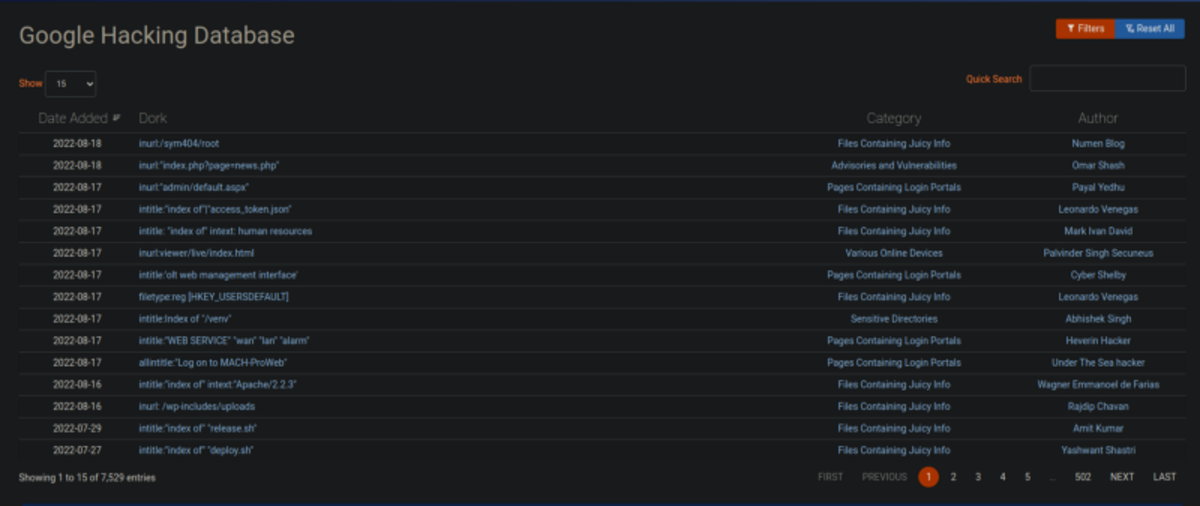
Google Dorking
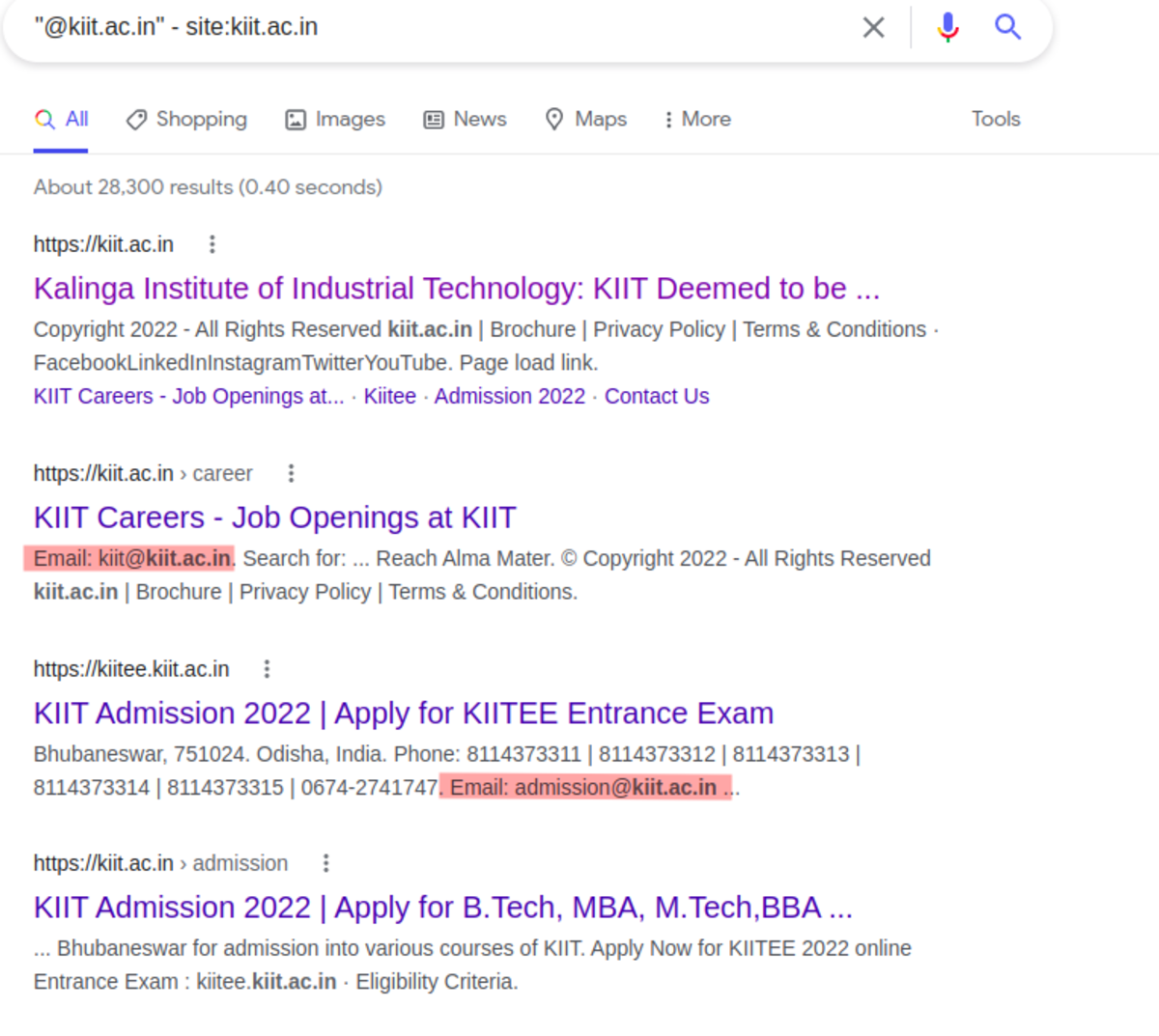
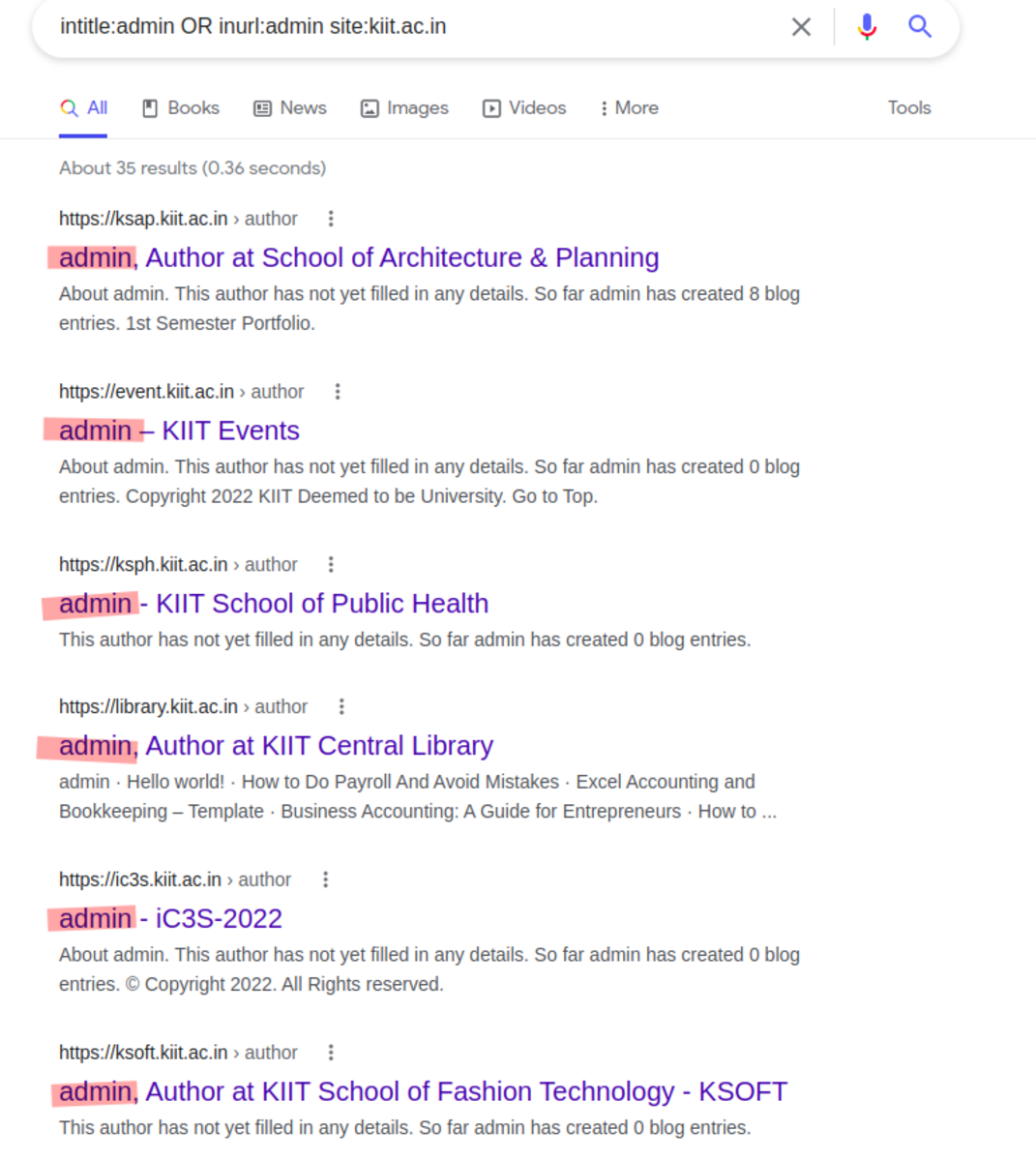
Using Google’s advanced search techniques to discover information that we might find useful. Ex. In google search, type the following site:tesla.com filetype: pdf // returns all the pdf files available on the website tesla.com Let’s find out some emails on the website “kiit.ac.in”. Searching the ‘admin’ keyword inside the title of the page or inside the URL. To find more useful commands on google dorks use “exploit-db.com”.
Ping, Host, Nslookup
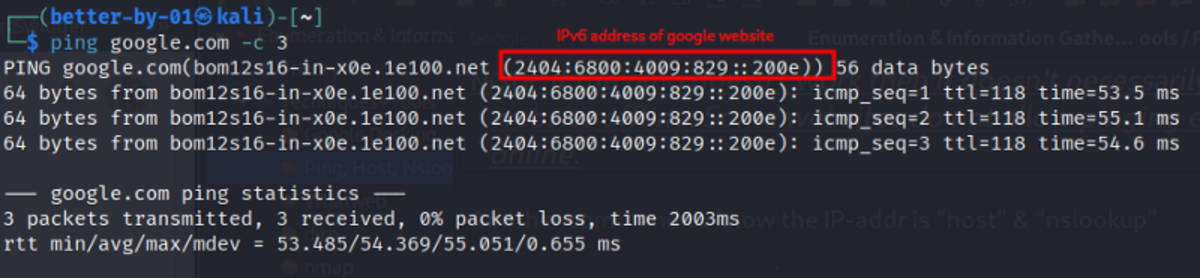
Ping
The “ping” command can be used to find the IP address of the website as well as to check if a particular website is up and running.
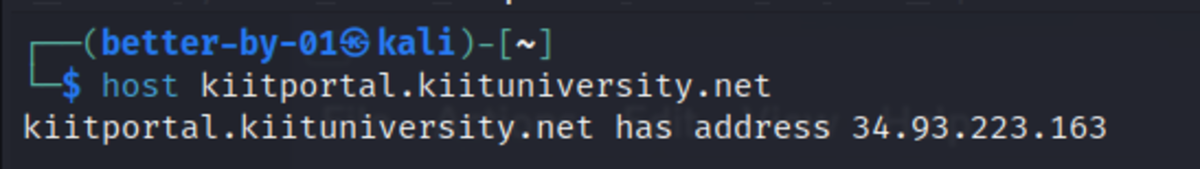
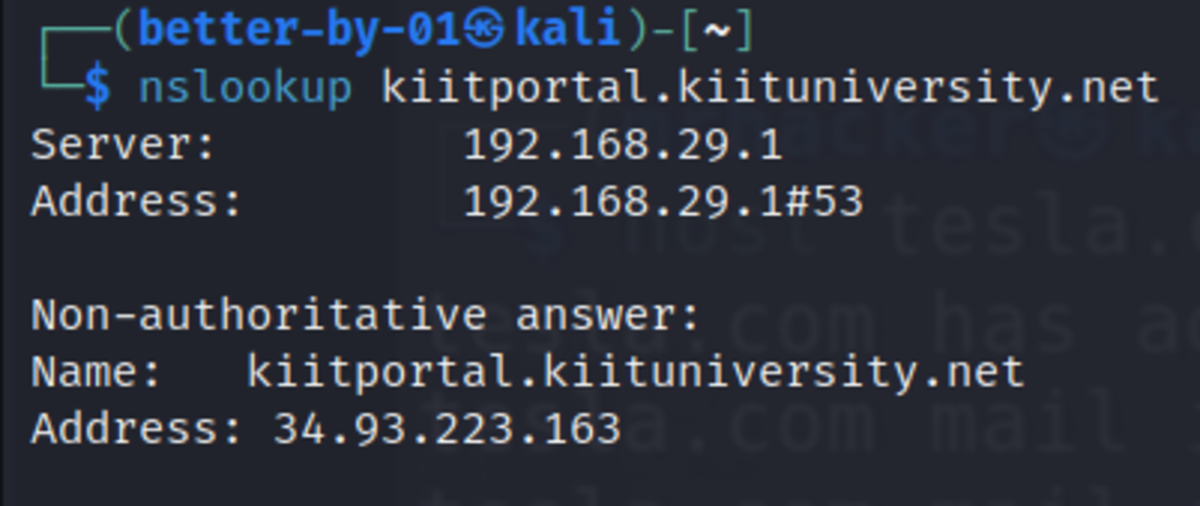
Host and Nslookup
Another command to know the IP address is “host” and “nslookup”.
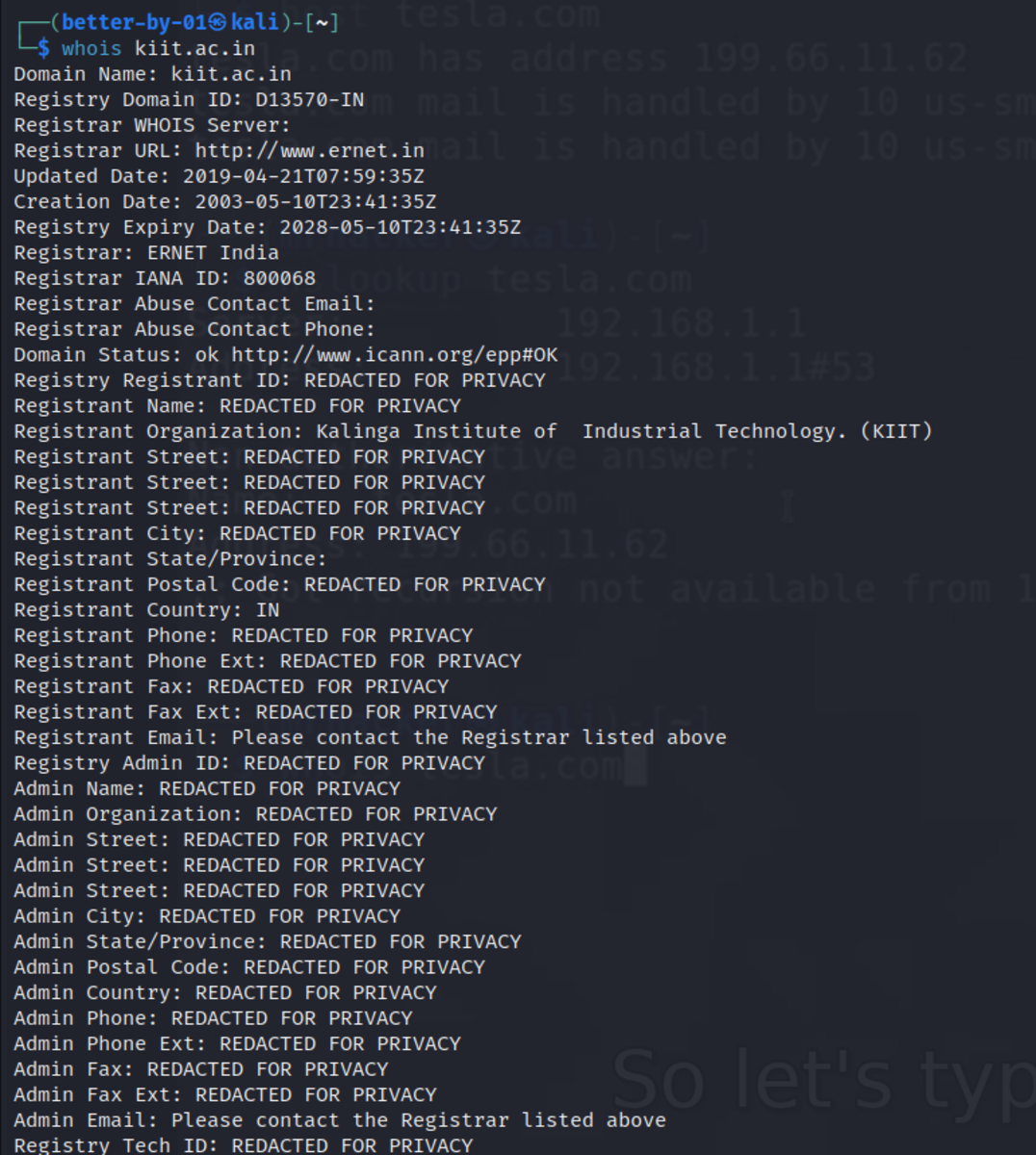
Whois
Used for gathering publicly available information about details of website registration that the owner of the website provides. Might also provide emails, phone numbers and physical addresses.
Active vs. Passive Information Gathering
When we were using the above commands we used active information gathering because we interacted with the website the whole time. Now if we use other websites to get the above information it will be passive information gathering because our target website won’t be able to see who searched that information for them because we never interacted with the website ourselves instead a third-party website did that task for us.
Example
Bonus Resources
This article is accurate and true to the best of the author’s knowledge. Content is for informational or entertainment purposes only and does not substitute for personal counsel or professional advice in business, financial, legal, or technical matters. © 2022 Ashutosh Singh Patel